Information Technology > QUESTIONS & ANSWERS > WGU C172 Network and Security Foundations Pre-Assessment Questions and Answers Graded A (All)
WGU C172 Network and Security Foundations Pre-Assessment Questions and Answers Graded A
Document Content and Description Below
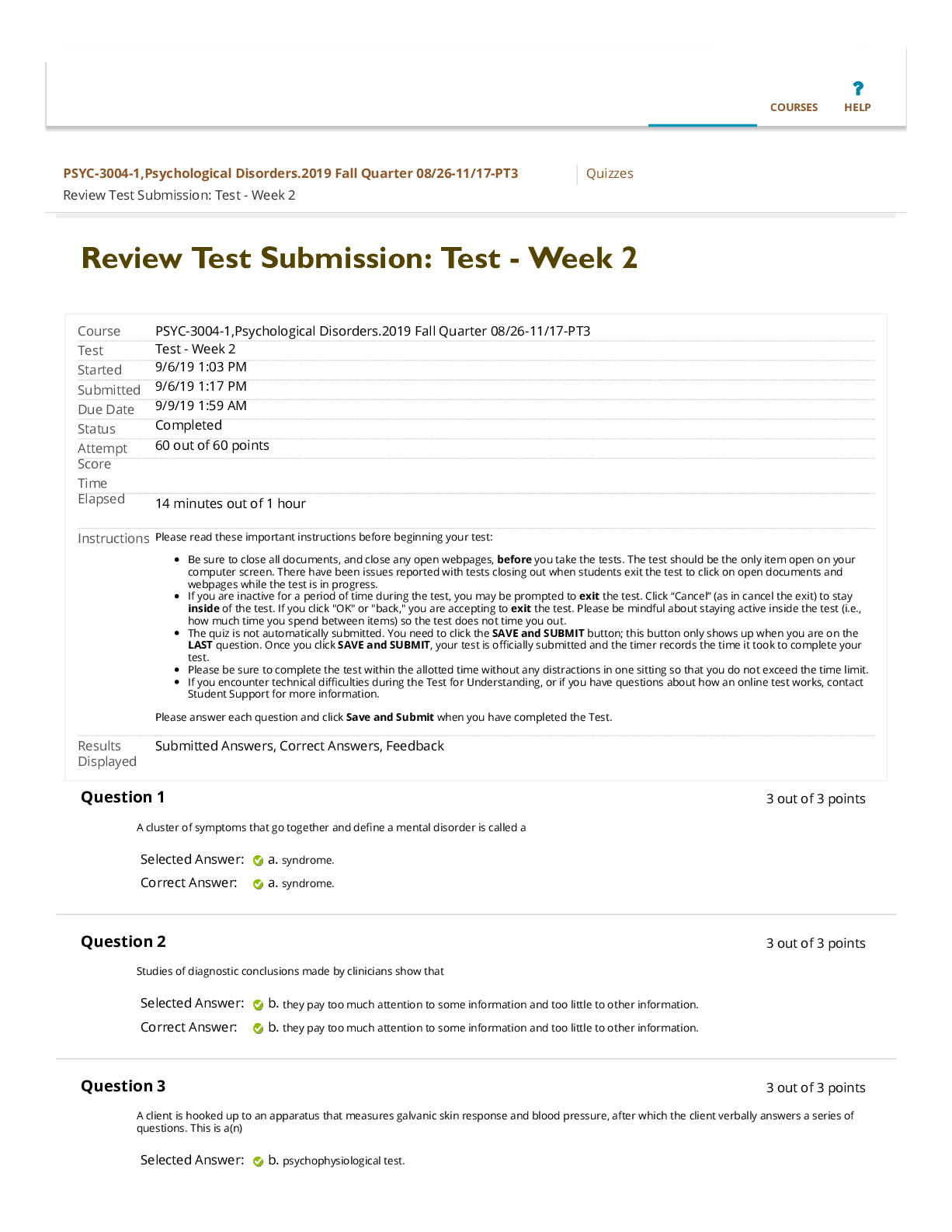
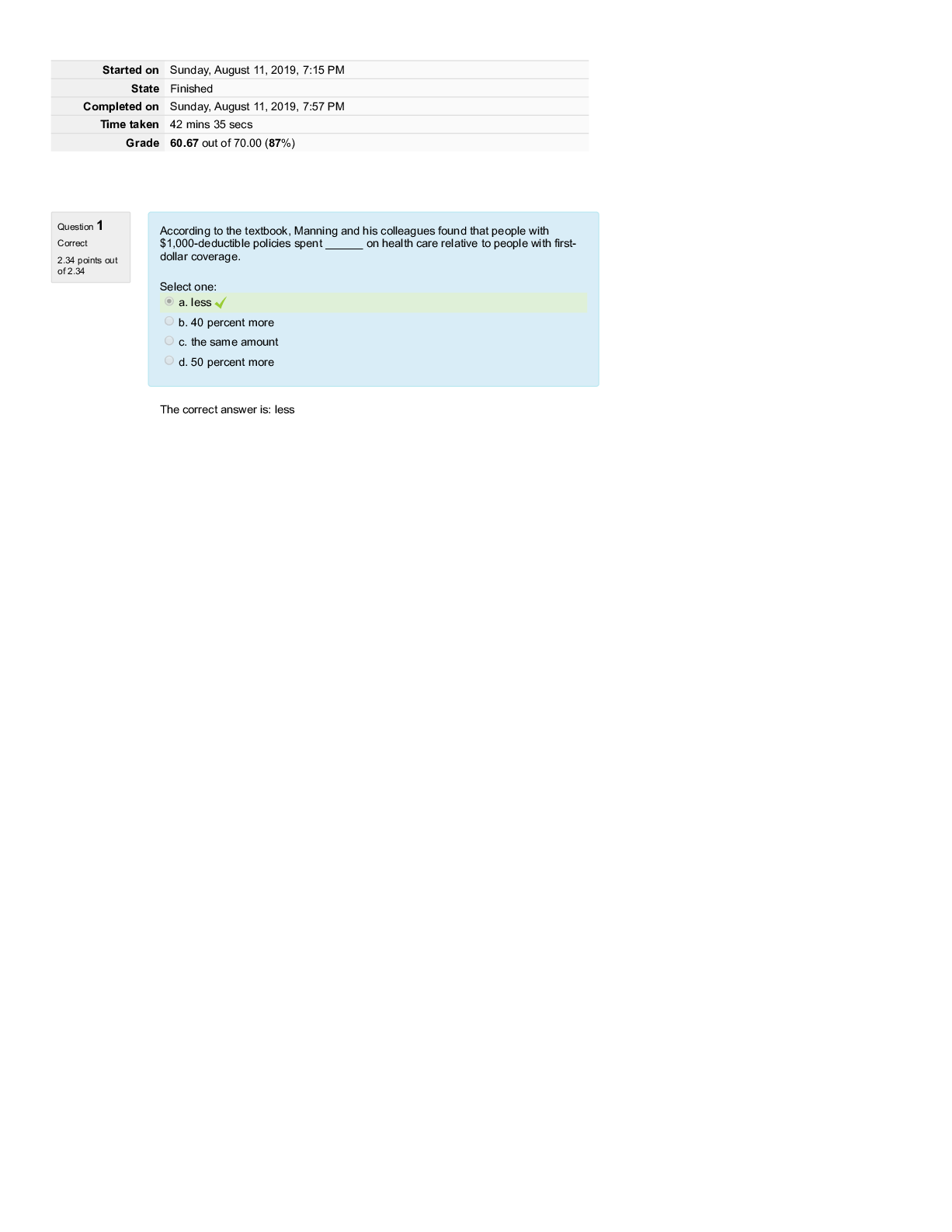
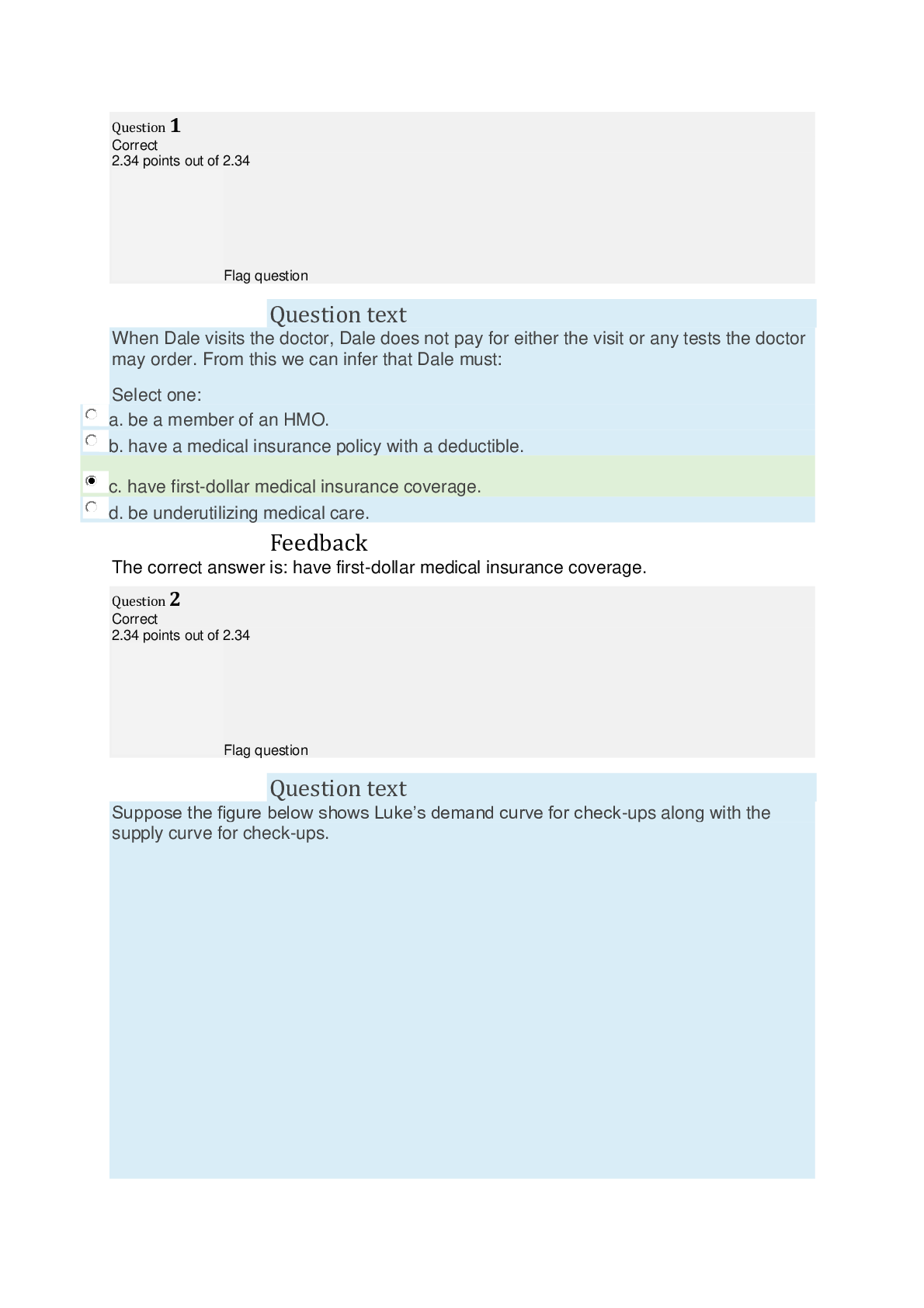
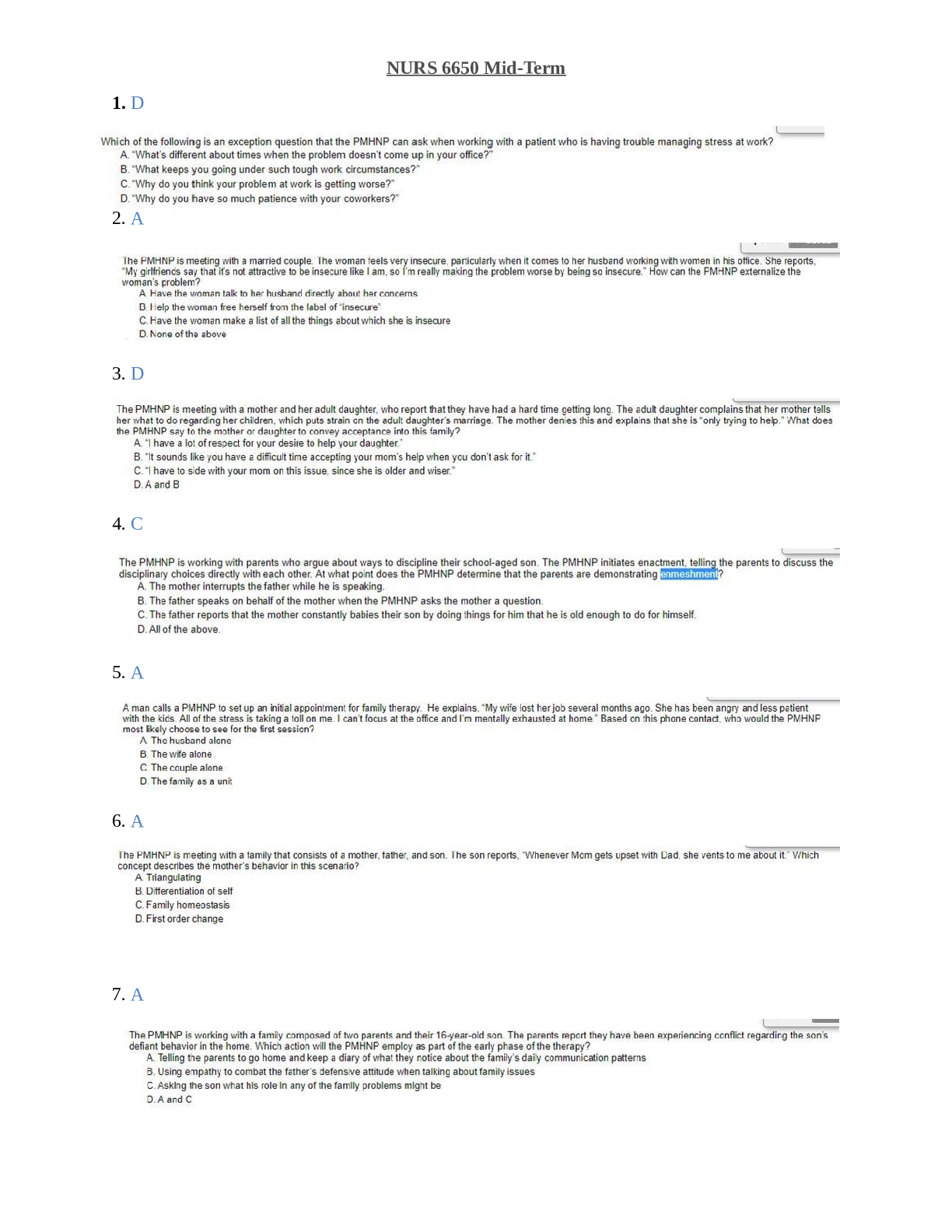
WGU C172 Network and Security Foundations Pre-Assessment Questions and Answers Graded A Which OSI(Open Systems Interconnection model) layer is related to the function of the IP protocol suite? ✔... ✔Network Which OSI(Open Systems Interconnection model) layer is responsible for organizing how bits are passed over the physical layer between devices within the same collision domain? ✔✔Data link Which OSI(Open Systems Interconnection model) layer would define the scope of a protocol that makes sure packets of data are received correctly and resends them if they are not? ✔✔Transport Which protocol suite performs functions of OSI(Open Systems Interconnection model) layer 4? ✔✔TCP(Transmission Control Protocol) Which type of Ethernet cable can maintain 10Gbps transmission speeds through the course of its maximum 100-meter length? ✔✔CAT 6a Which Internet access technology uses ordinary telephone wires for data transmission? ✔✔DSL(Digital Subscriber Line) Which device is used to organize network cables as they run between switches and other network devices? ✔✔Patch panel Which network device is used to connect two or more network segments by performing OSI layer 3 functions like packet-forwarding? ✔✔Router Which network device is used to convert between digital information from a LAN and analog signals for transmission over a standard telephone wire? ✔✔Modem Which device could be used to send commands to the mainframe for remote execution in early mainframe installations? ✔✔Dumb terminals Which device is responsible for implementing network address translation (NAT)? ✔✔Router Which command produces the following output? Non-authoritative answer: Name: www.google.com Address: 172.217.11.132 ✔✔nslookup Which command should be used to manually enter the default gateway for a computer? ✔✔route Which network diagnostic tool displays the path packets take between two endpoints? ✔✔raceroute Which network type is used to wire multiple PCs to a home router? ✔✔LAN(Local Area Network) An office's infrastructure connects network devices and printers through a central access point without the use of cabling. Which network type does this office use? ✔✔WLAN(Wireless Local Area Network) What type of medium is commonly used within a 1000 Mbps Ethernet network? ✔✔CAT5e Which network topology is shown in the following diagram? ✔✔Full mesh Which networking standard uses UTP(Unshielded Twisted Pair) cable and CSMA/CD(Carriersense multiple access with collision detection) to manage connected devices' access to the wire? ✔✔Ethernet Which network topology is being implemented when each node connects to exactly two other nodes, forming a single continuous pathway for signals through each node? ✔✔Ring In which physical LAN topology are nodes connected to each other with a backbone cable that loops around and ends at the same point it started? ✔✔Ring Which OSI(Open Systems Interconnection) layer ensures error-free packets? ✔✔Transport Which topology uses a switch or hub to connect to all devices in the same network? ✔✔Star Which cloud service provides hardware, operating systems, and web servers but not end-user applications? ✔✔PaaS (Platform-as-a-service) Which cloud model provides an exclusive cloud computing service environment that is shared between two or more organizations? ✔✔Community Which type of software is used to provide virtualization? ✔✔Hypervisor A user that does not want to be identified while communicating on a network uses an application to alter the computer's identity. Which type of exploit is being perpetrated? ✔✔Spoofing An attacker attempts to misdirect traf c on a network back to the attacker by corrupting the network computer's cache of IP address to MAC address mappings that are cached. Which exploit is the attacker perpetrating? ✔✔ARP(Address Resolution Protocol) poisoning Which exploit actually breaches the physical medium or uses devices to monitor signals from outside the physical medium itself? ✔✔Wiretapping Which type of attack can overwhelm a web server by inserting more data into a web form than the system was con gured to hold? ✔✔Buffer overflow Which type of attack sends an email claiming to be from a reputable business in order to entice the recipient to provide sensitive information? ✔✔Phishing A user on a network is planning to launch an exploit against a coworker in a neighboring department. The user needs to identify the IP address of a coworker in the desired department. Which tool or utility will allow the user to watch network traf c in real time to identify a target? ✔✔Sniffer Which group of attackers is typical [Show More]
Last updated: 1 year ago
Preview 1 out of 12 pages
Instant download
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
Also available in bundle (1)
.png)
WGU C172 Network and Security – Foundations Bundled Questions and Answers Latest Update Already Passed
WGU C172 Network and Security – Foundations Bundled Questions and Answers Latest Update Already Passed
By Nutmegs 1 year ago
$20
10
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Aug 16, 2022
Number of pages
12
Written in
Additional information
This document has been written for:
Uploaded
Aug 16, 2022
Downloads
0
Views
96

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)




.png)

.png)

.png)

