Computer Science > QUESTIONS & ANSWERS > WGU C836 MULTI/COMPREHENSIVE FINAL EXAM REVIEW (LATEST VERSION 2022) (All)
WGU C836 MULTI/COMPREHENSIVE FINAL EXAM REVIEW (LATEST VERSION 2022)
Document Content and Description Below
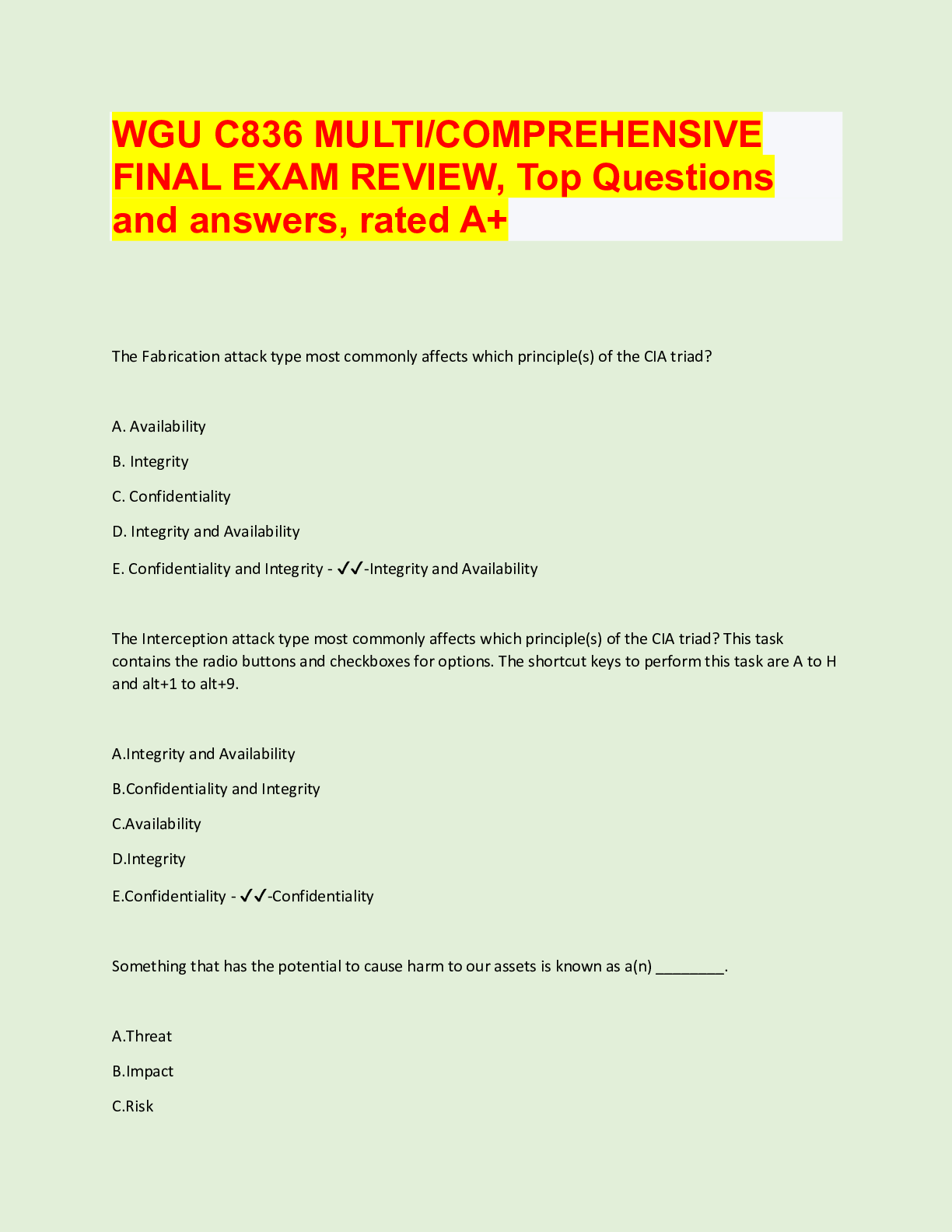
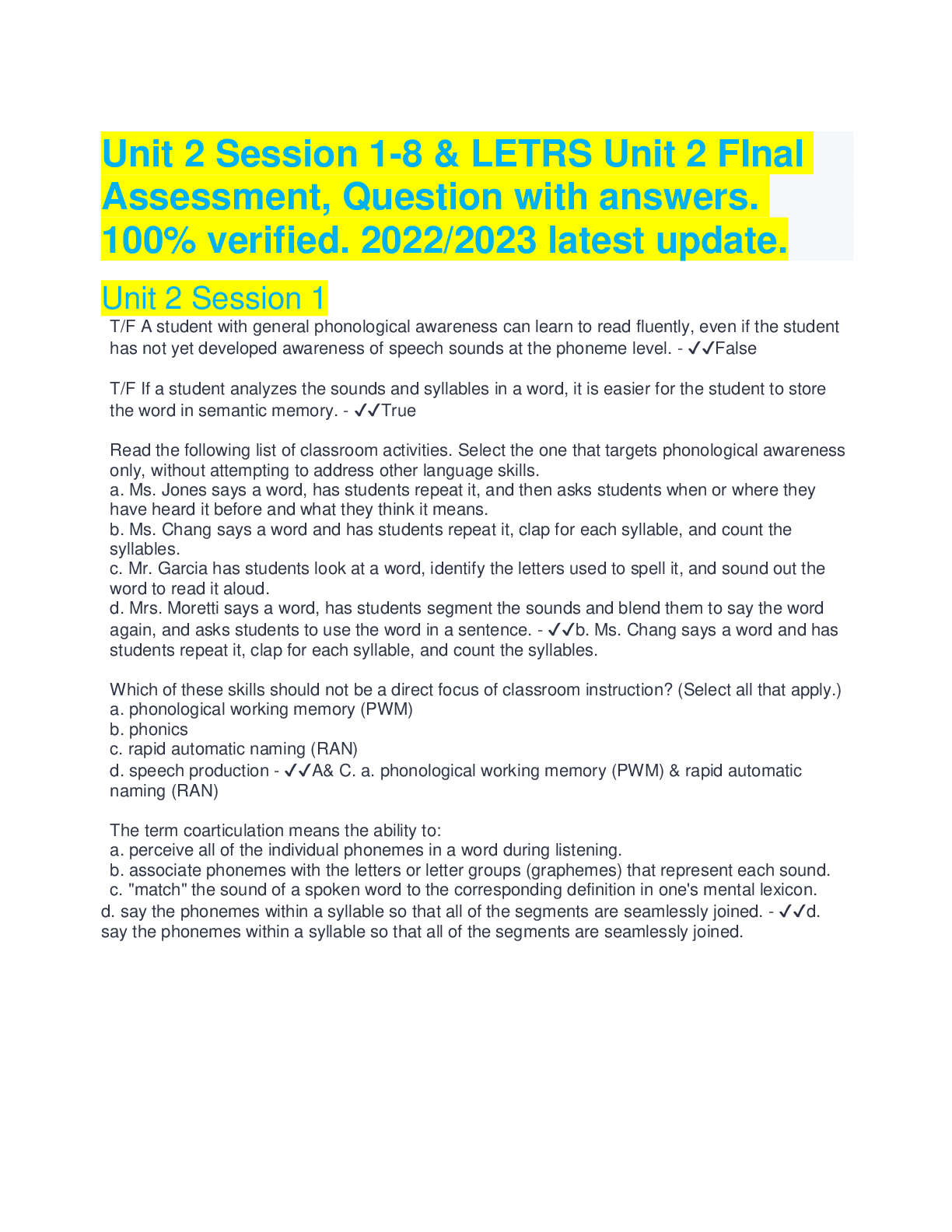
WGU C836 MULTI/COMPREHENSIVE FINAL EXAM REVIEW (LATEST VERSION 2022) ______ regulates the financial practice and governance of corporations. This task contains the radio buttons and checkboxes for... options. The shortcut keys to perform this task are A to H and alt+1 to alt+9. A.GLBA B.FISMA C.SOX D.FERPA E.HIPAA Correct Answer- C.SOX _______ provides us with the means to trace activities in our environment back to their source. This task contains the radio buttons and checkboxes for options. The shortcut keys to perform this task are A to H and alt+1 to alt+9. A.Access B.Authentication C.Accountability D.Authorization E.Nonrepudiation Correct Answer- C.Accountability _____________ is a popular, fully-featured sniffer capable of intercepting traffic from a wide variety of wired and wireless sources. A.WiresharkB.Kismet C.Hping3 D.NetStumbler Correct Answer- A.Wireshark _____________ is a sniffer that specializes in detecting wireless devices. A.Hping3 B.Kismet C.Wireshark D.NetStumbler Correct Answer- B.Kismet A combination of a network design feature and a protective device such as a firewall; often used for systems that need to be exposed to external networks but are connected to our network (such as a web server) Correct Answer- Demilitarized Zone (DMZ) A combination of DAC and MAC, primarily concerned with the confidentiality of the resource. Two security properties define how information can flow to and from the resource: the simple security property and the * property. Correct Answer- The Bell-LaPadula model A database is vulnerable to SQL injection attacks through direct attempts to the database server or through applications software, including web applications. What is the most effective way of mitigating these attacks? A.Authenticating the user on the client-side B.Authenticating the user on the server-side C.Keeping the software patched D.Turning on database logging E.Validating user inputs Correct Answer- E.Validating user inputsA firewall technology that can analyze the actual content of the traffic that is flowing through Correct Answer- Deep packet inspection A firewall technology that functions on the same general principle as packet filtering firewalls, but is able to keep track of the traffic at a granular level. Has the ability to watch the traffic over a given connection Correct Answer- Stateful packet inspection A firewall technology that inspects the contents of each packet in network traffic individually and makes a gross determination (based on source and destination IP address, port number, and the protocol being used) of whether the traffic should be allowed to pass Correct AnswerPacket filtering A firewall that can watch packets and monitor the traffic from a given connection is using what kind of firewall technology? A.Deep packet inspection B.Stateful packet inspection C.Packet filtering Correct Answer- B.Stateful packet inspection A fully featured sniffer that is also a great tool for troubleshooting traffic; this well-known tool is used by many network operations and security teams Correct Answer- Wireshark A group of tools that can include network mapping tools, sniffers, and exploits Correct AnswerExploit framework A hardware- and software-based technology that prevents certain portions of the memory used by the operating system and applications from being used to execute code Correct AnswerExecutable space protection A model that adds three more principles to the CIA triad: possession or control, utility, and authenticity Correct Answer- Parkerian hexadA multilayered defense that will allow us to achieve a successful defense should one or more of our defensive measures fail Correct Answer- Defense in depth A particularly complex and impactful item of malware that targeted the Supervisory Control and Data Acquisition (SCADA) systems that run various industrial processes; this piece of malware raised the bar for malware from largely being a virtual-based attack to actually being physically destructive Correct Answer- Stuxnet A phrase that refers to an organization's strategy and policies regarding the use of personal vs. corporate devices Correct Answer- Bring your own device (BYOD A principle that states we should only allow a party the absolute minimum permission needed for it to carry out its function Correct Answer- The principle of least privilege A program that seeks to make users aware of the risk they are accepting through their current actions and attempts to change their behavior through targeted efforts Correct AnswerSecurity Awareness, Training, and Education (SATE) A security method that involves shifting the contents of memory around to make tampering difficult Correct Answer- Address space layout randomization (ASLR) A set of symmetric block ciphers endorsed by the US government through NIST. Shares the same block modes that DES uses and also includes other modes such as XEX-based Tweaked CodeBook (TCB) mode Correct Answer- AES A social engineering technique that targets a specific company, organization, or person, and involves knowing specifics about the target to appear valid Correct Answer- Spear phishing A social engineering technique that uses electronic communications (email, texts, or phone calls) to convince a potential victim to give out sensitive information or perform some action Correct Answer- PhishingA specialized type of firewall that can serve as a choke point, log traffic for later inspection, and provide a layer of security for the devices behind it Correct Answer- Proxy server A specialized type of firewall that provides security and performance features, functions as a choke point, allows for logging traffic for later inspection, and serves as a single source of requests for the devices behind it is known as a(n) ____________ A.Proxy server B.FTP server C.Packet sniffer D.Web server E.Intrusion detection system Correct Answer- A.Proxy server [Show More]
Last updated: 1 year ago
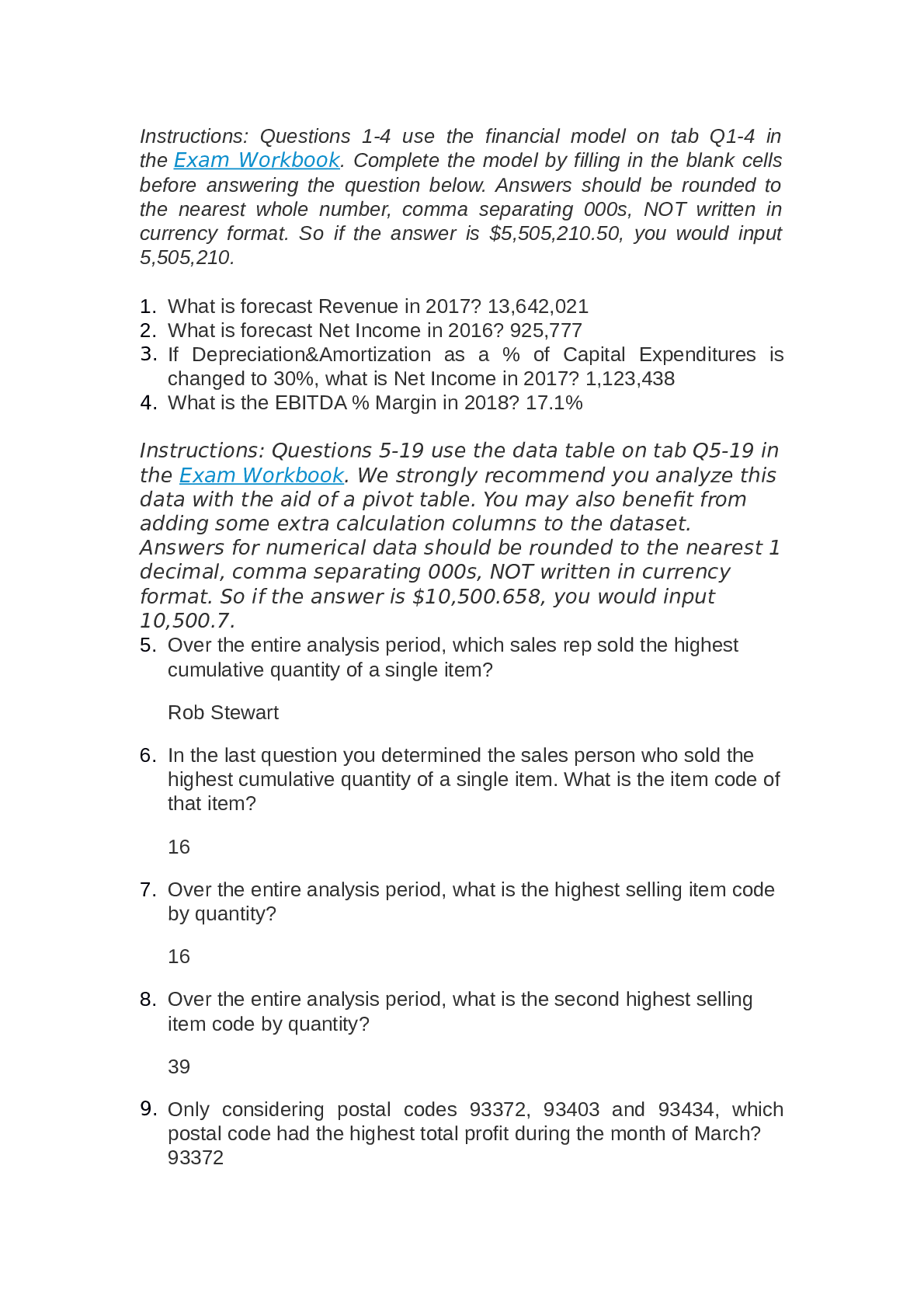
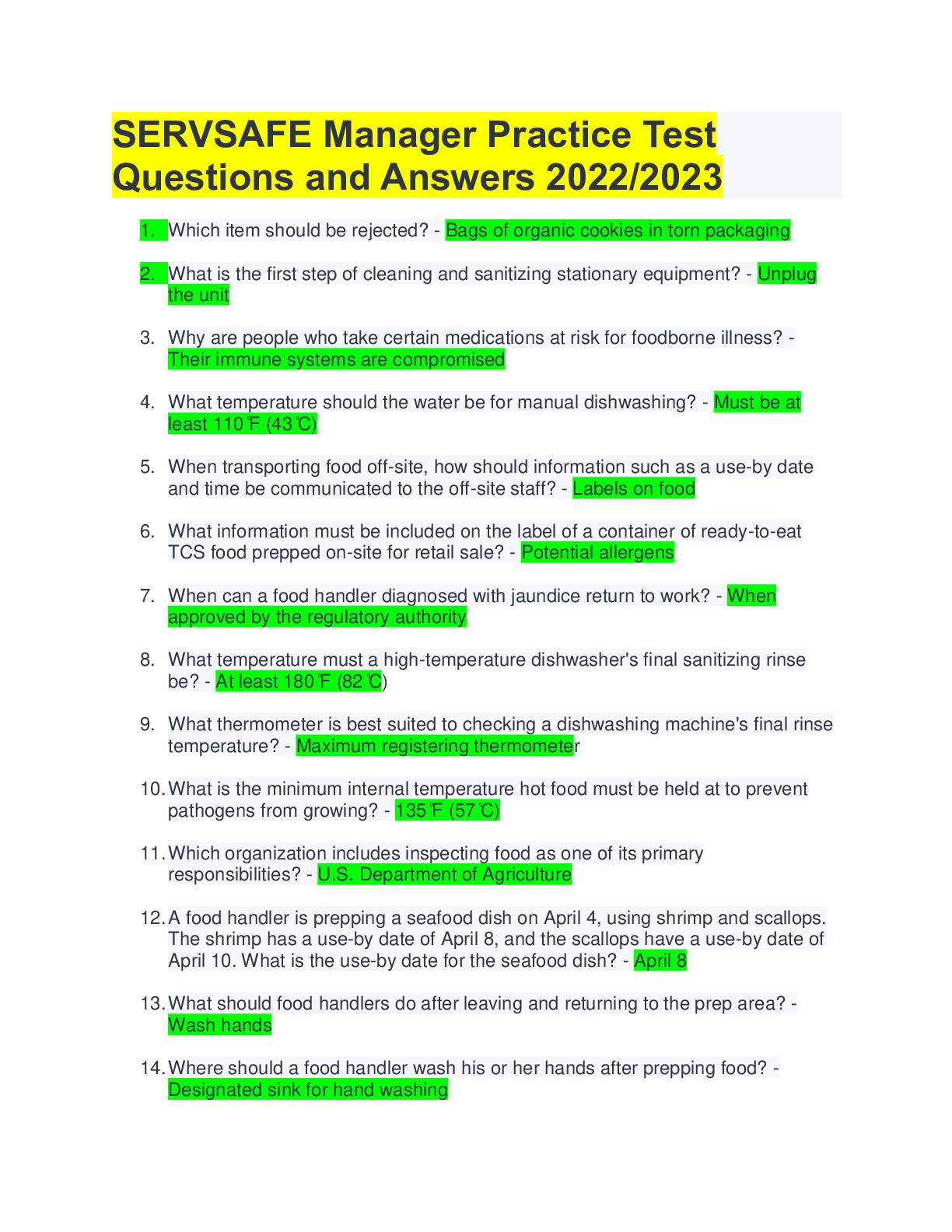
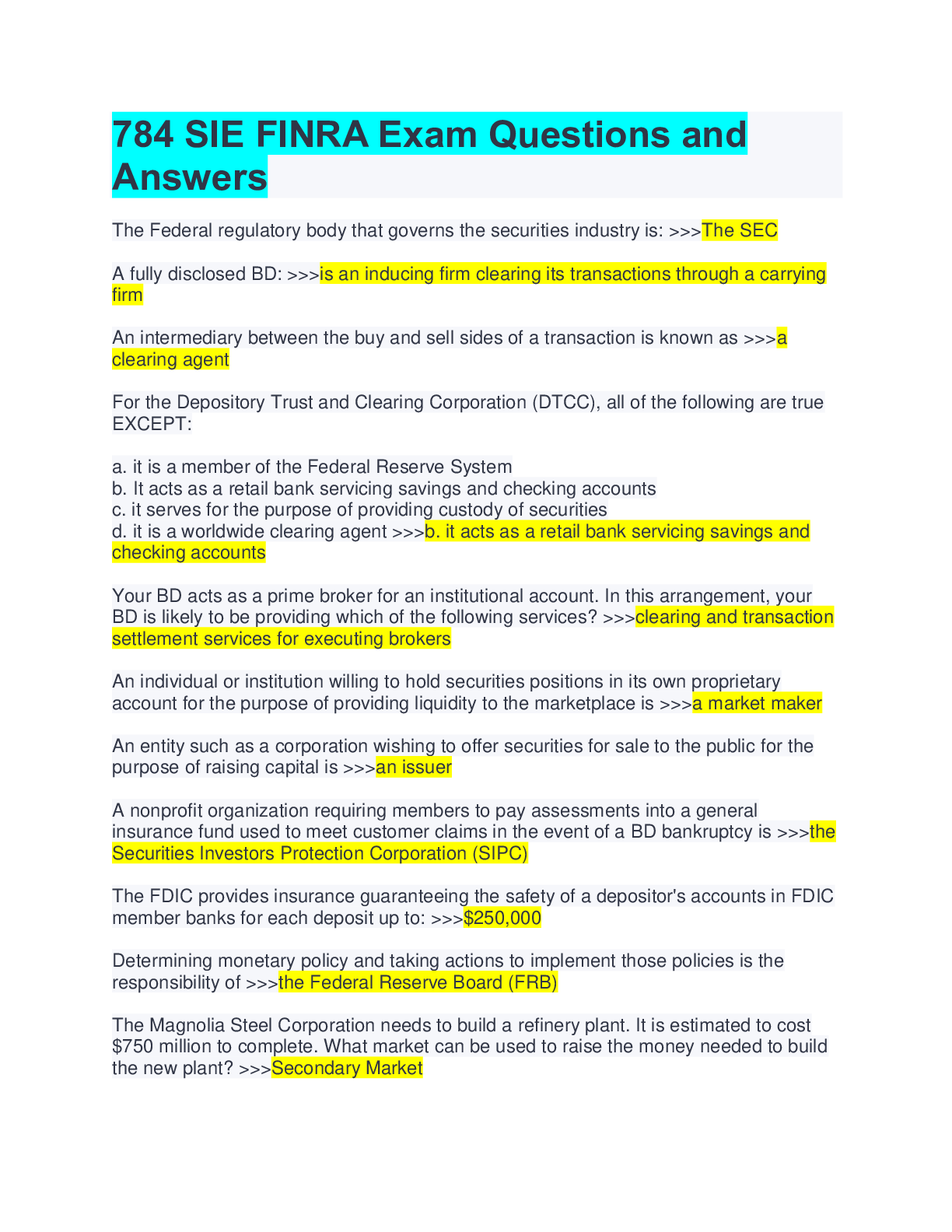
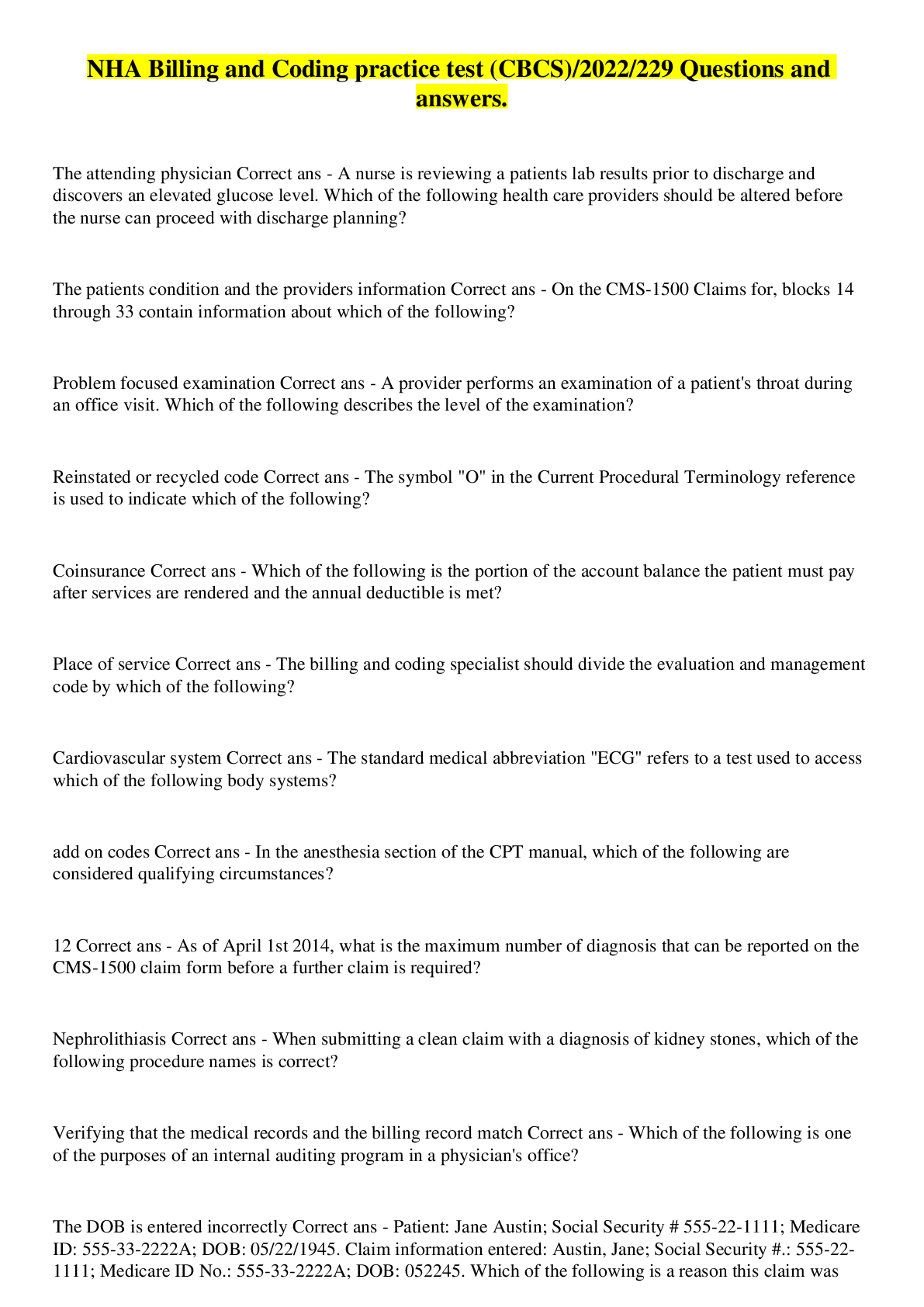
Preview 1 out of 33 pages
.png)
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Sep 19, 2022
Number of pages
33
Written in
Additional information
This document has been written for:
Uploaded
Sep 19, 2022
Downloads
0
Views
74












.png)
.png)
.png)



.png)
.png)




.png)
.png)

