Information Technology > QUESTIONS & ANSWERS > WGU C795 NOC REPORTING TEMPLATE LATEST UPDATED 2022 (All)
WGU C795 NOC REPORTING TEMPLATE LATEST UPDATED 2022
Document Content and Description Below
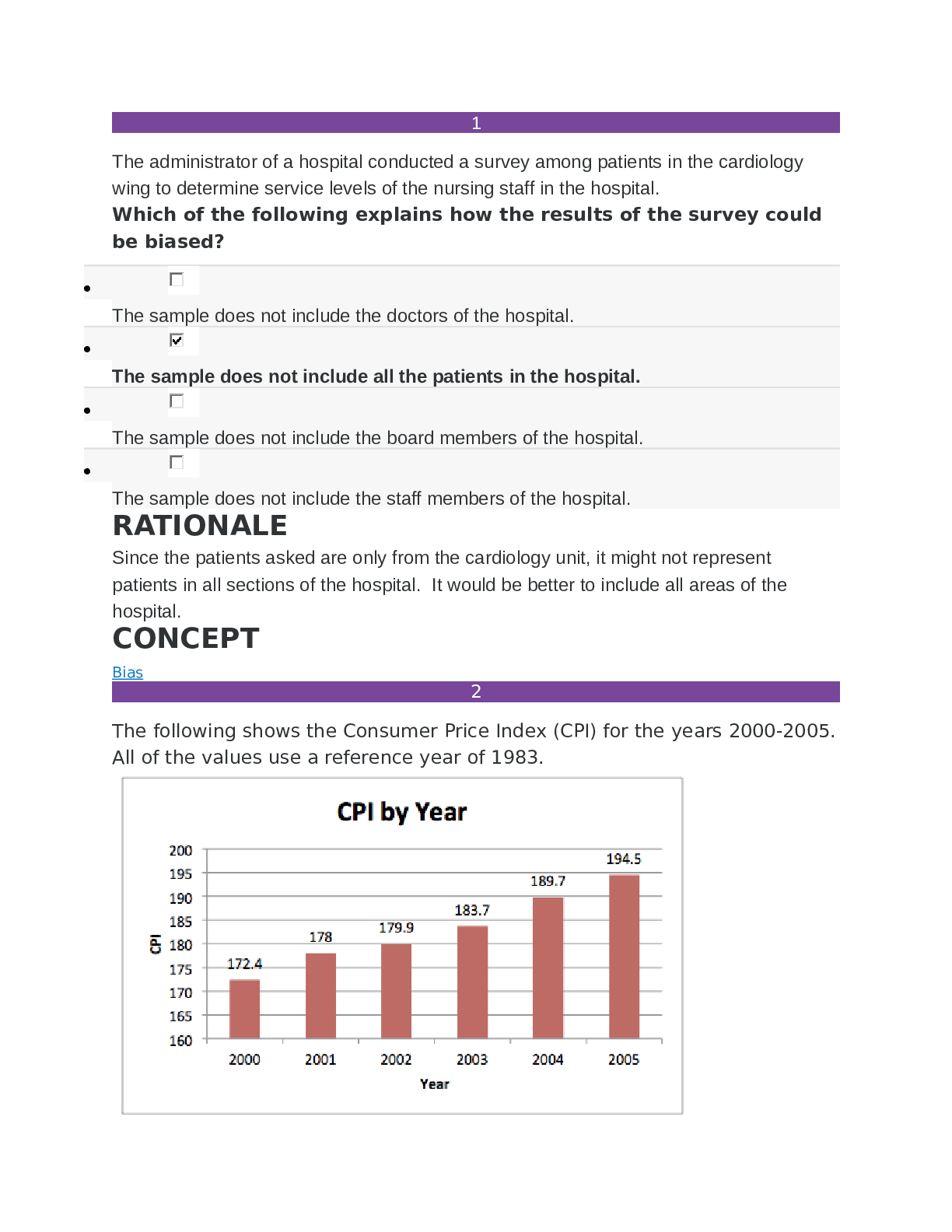
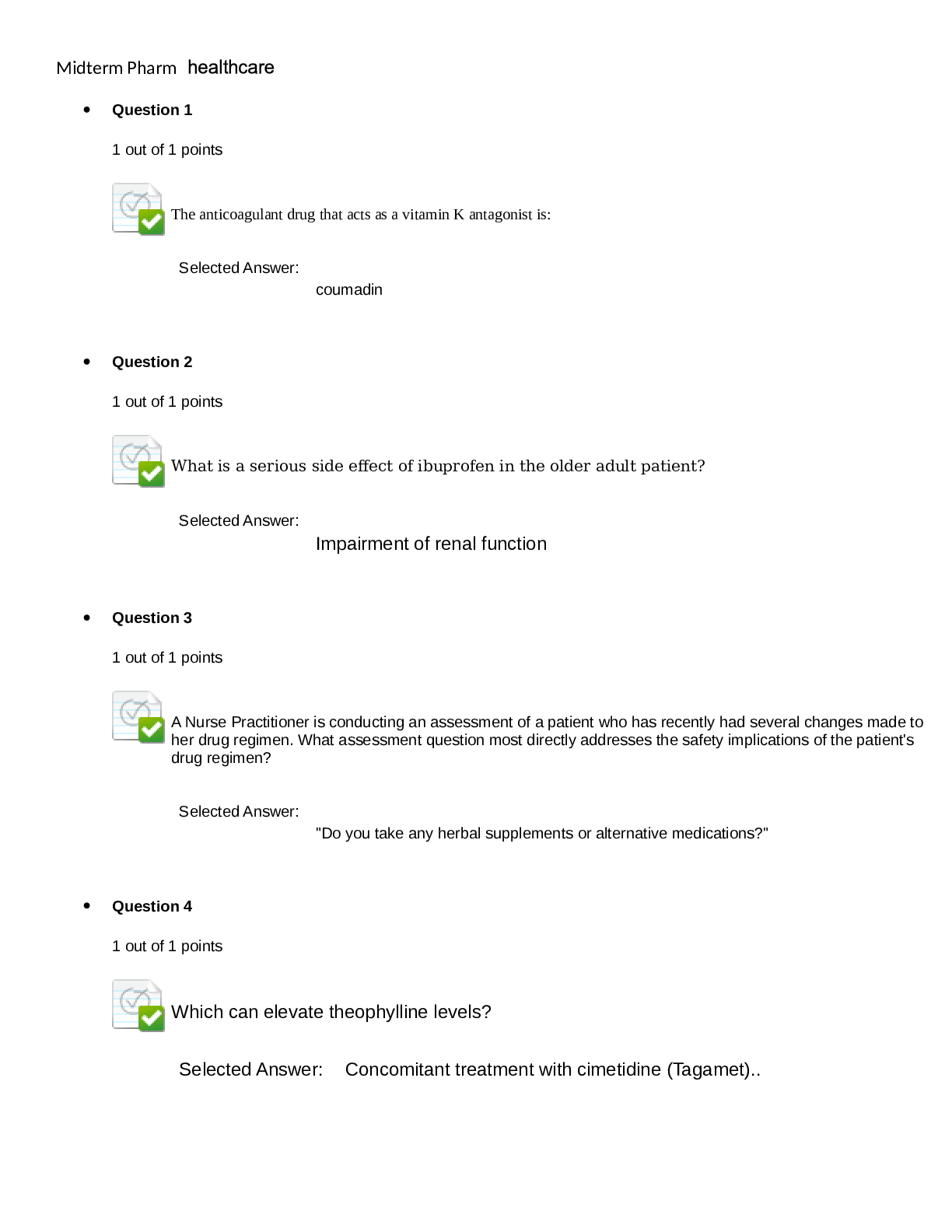
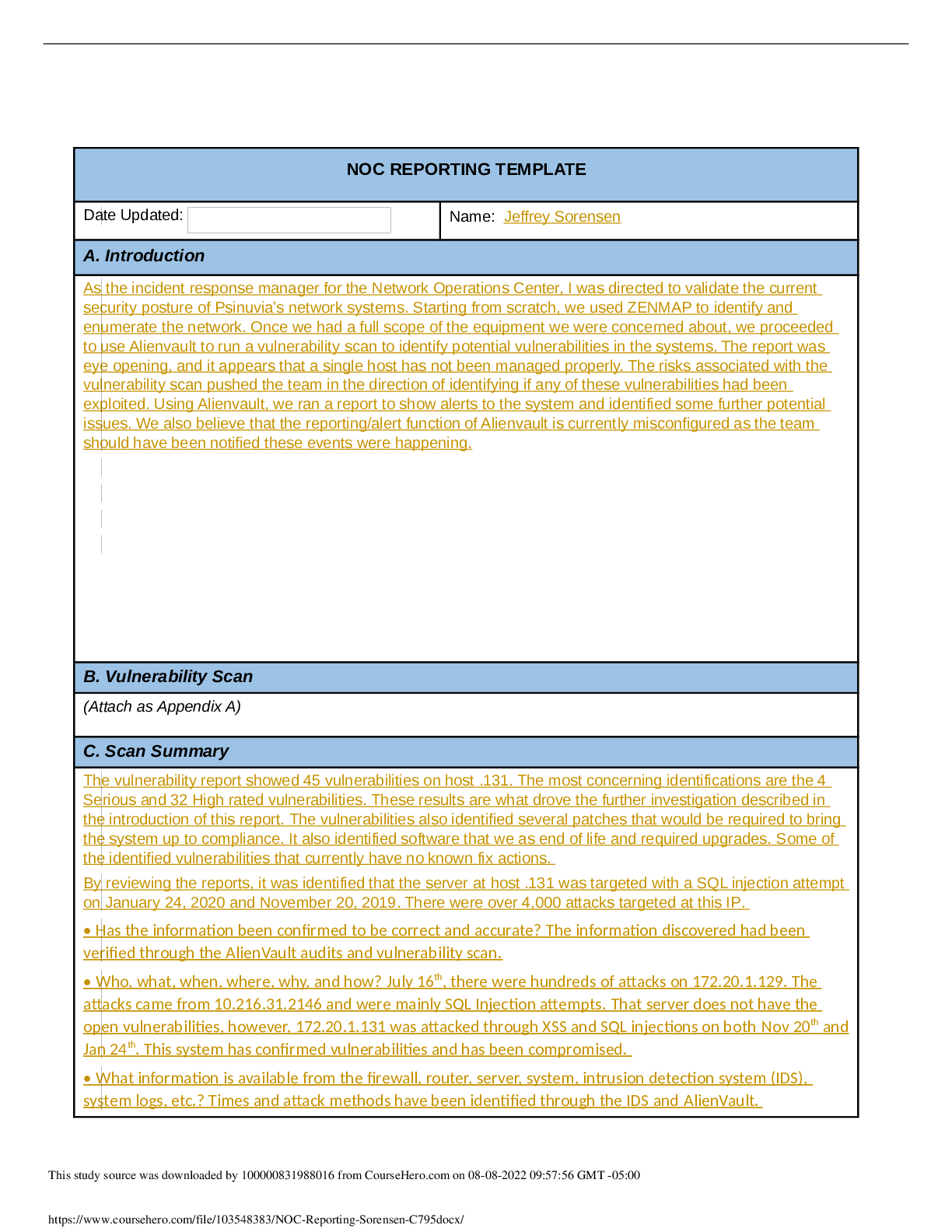
NOC REPORTING TEMPLATE Date Updated: Name: Jeffrey Sorensen A. Introduction As the incident response manager for the Network Operations Center, I was directed to validate the current security post... ure of Psinuvia’s network systems. Starting from scratch, we used ZENMAP to identify and enumerate the network. Once we had a full scope of the equipment we were concerned about, we proceeded to use Alienvault to run a vulnerability scan to identify potential vulnerabilities in the systems. The report was eye opening, and it appears that a single host has not been managed properly. The risks associated with the vulnerability scan pushed the team in the direction of identifying if any of these vulnerabilities had been exploited. Using Alienvault, we ran a report to show alerts to the system and identified some further potential issues. We also believe that the reporting/alert function of Alienvault is currently misconfigured as the team should have been notified these events were happening. B. Vulnerability Scan (Attach as Appendix A) C. Scan Summary The vulnerability report showed 45 vulnerabilities on host .131. The most concerning identifications are the 4 Serious and 32 High rated vulnerabilities. These results are what drove the further investigation described in the introduction of this report. The vulnerabilities also identified several patches that would be required to bring the system up to compliance. It also identified software that we as end of life and required upgrades. Some of the identified vulnerabilities that currently have no known fix actions. By reviewing the reports, it was identified that the server at host .131 was targeted with a SQL injection attempt on January 24, 2020 and November 20, 2019. There were over 4,000 attacks targeted at this IP. • Has the information been confirmed to be correct and accurate? The information discovered had been verified through the AlienVault audits and vulnerability scan. • Who, what, when, where, why, and how? July 16th , there were hundreds of attacks on 172.20.1.129. The attacks came from 10.216.31.2146 and were mainly SQL Injection attempts. That server does not have the open vulnerabilities, however, 172.20.1.131 was attacked through XSS and SQL injections on both Nov 20th and Jan 24th . This system has confirmed vulnerabilities and has been compromised. • What information is available from the firewall, router, server, system, intrusion detection system (IDS), system logs, etc.? Times and attack methods have been identified through the IDS and AlienVault. This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 09:57:56 GMT -05:00 https://www.coursehero.com/file/103548383/NOC-Reporting-Sorensen-C795docx/ • What type of data is involved, and what is its classification? All data involved is unclassified. However, it is possible that there is both medical data and PII that could only be disclosed under the proper reasoning and procedures. • Are there obscenities, child pornography, or confrontational data? There is no obscene or vulgar data involved. • Is there criminal activity? At the current time, criminal activity is not suspected. • Is the data protected by an encryption solution? Data is protected by encryption. • What is the magnitude of the systems being impacted? Magnitude of the system is high. The data being tracked is significantly impacting overall health of patients. • Is the event still in progress? Yes • Has preliminary containment been performed (i.e., disable account, reset password, remove remote access, isolate device in segregated segment)? System has been disabled and removed from the network. • What is the estimated value of the impacted data and systems? Data is valued at ~$200M (~1/3 of yearly sales) and the system is ~$10K D. Detailed Analysis Reviewing the SIEM identified several different attacks that happened from July to January. Starting with the earlier attacks, alarms were reviewed and monitored to identify which systems were being attacked and if they were vulnerable to those attacks. In July, the attacks were targeted at system 129. These attacks mainly consisted of SQL injection attempts with a few XSS and brute force attacks. But as identified in the Vulnerability report, this system is secure. This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 09:57:56 GMT -05:00 https://www.coursehero.com/file/103548383/NOC-Reporting-Sorensen-C795docx/ Then next step was to review the alarms that were triggered in November. Systems 129 and 131 were both targeted during this attack. Again system 129 is secure according to the vulnerability scan, but most attacks were targeting 131. Resources were targeted to identifying the capabilities of the system and if it had been exploited. Per the vulnerability scan, this system is missing multiple updates and has several issues as identified in section C of this document. The images below show both the summary of alarms per host and some of the specific events that triggered the alarms. This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 09:57:56 GMT -05:00 https://www.coursehero.com/file/103548383/NOC-Reporting-Sorensen-C795docx/ The final step was to look at the events of January 24th . There is a persistent threat to the network as this is the third example of similar attack patterns. Again, system 131 was the primary target and it had not been patched since the events of November. The images below show both the summary of alarms per host and some of the specific events that triggered the alarms. This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 09:57:56 GMT -05:00 [Show More]
Last updated: 1 year ago
Preview 1 out of 7 pages
Instant download
Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Aug 08, 2022
Number of pages
7
Written in
Additional information
This document has been written for:
Uploaded
Aug 08, 2022
Downloads
0
Views
177

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)