Computer Networking > QUESTIONS & ANSWERS > EC-Council CHFI Test Questions & Answers (All)
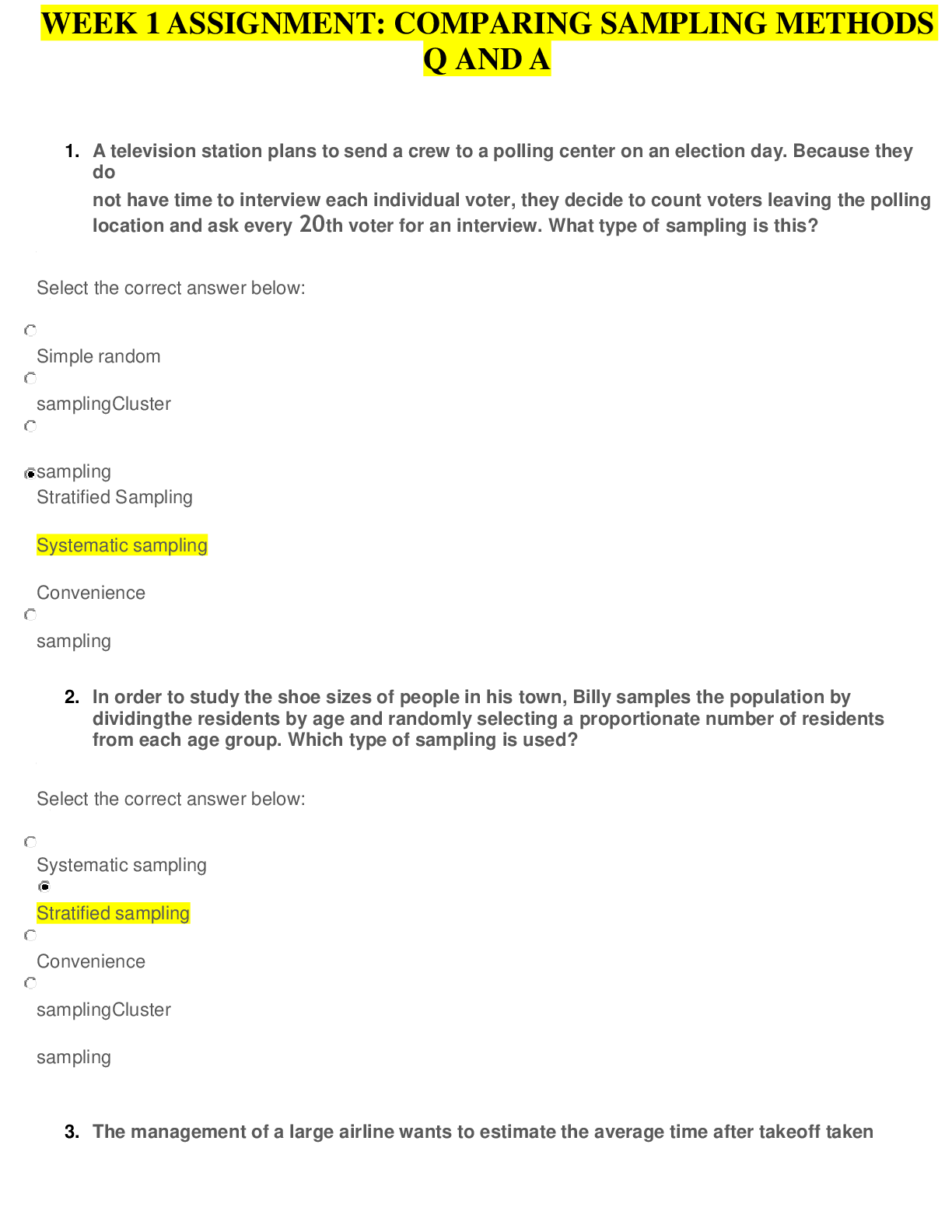
EC-Council CHFI Test Questions & Answers
Document Content and Description Below
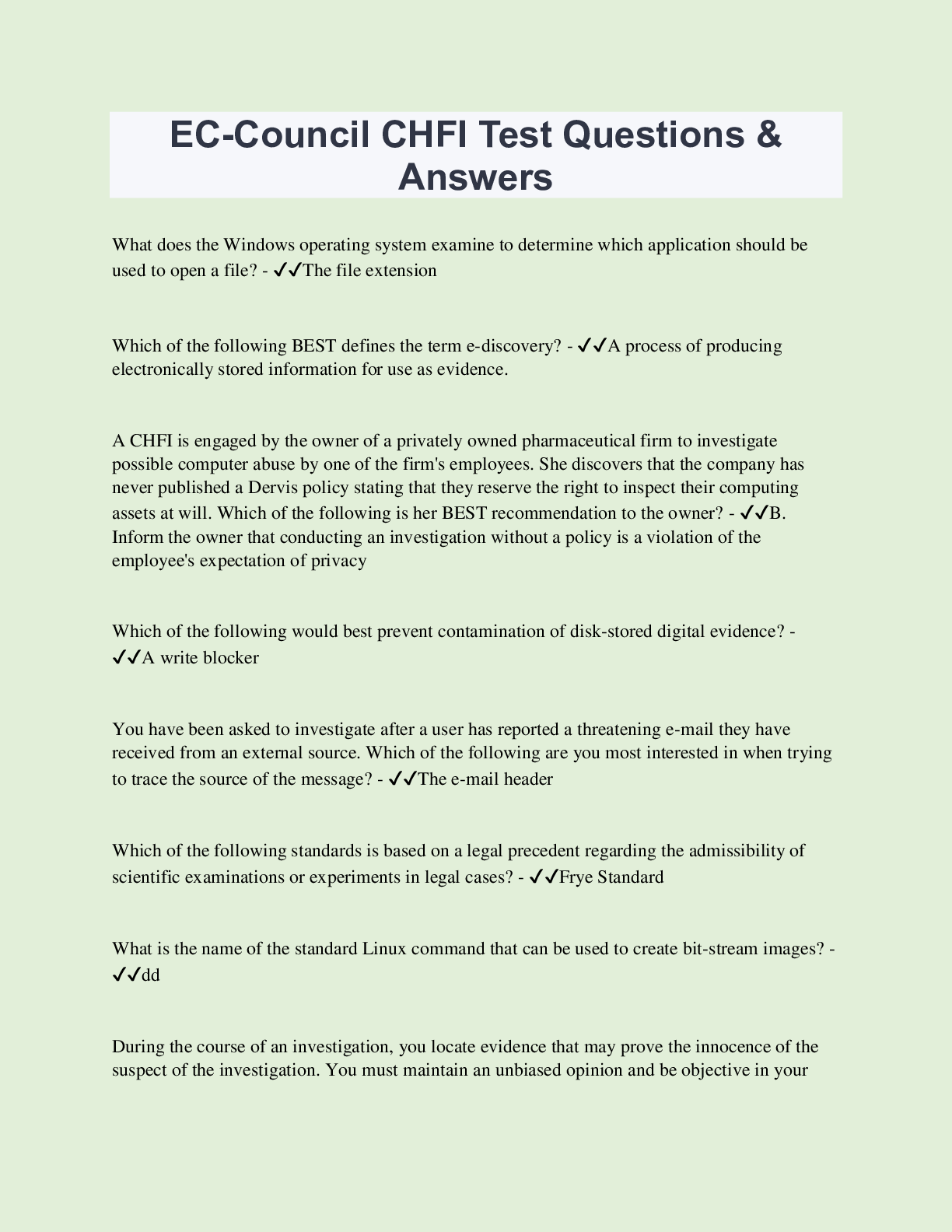
EC-Council CHFI Test Questions & Answers What does the Windows operating system examine to determine which application should be used to open a file? - ✔✔The file extension Which of the follow... ing BEST defines the term e-discovery? - ✔✔A process of producing electronically stored information for use as evidence. A CHFI is engaged by the owner of a privately owned pharmaceutical firm to investigate possible computer abuse by one of the firm's employees. She discovers that the company has never published a Dervis policy stating that they reserve the right to inspect their computing assets at will. Which of the following is her BEST recommendation to the owner? - ✔✔B. Inform the owner that conducting an investigation without a policy is a violation of the employee's expectation of privacy Which of the following would best prevent contamination of disk-stored digital evidence? - ✔✔A write blocker You have been asked to investigate after a user has reported a threatening e-mail they have received from an external source. Which of the following are you most interested in when trying to trace the source of the message? - ✔✔The e-mail header Which of the following standards is based on a legal precedent regarding the admissibility of scientific examinations or experiments in legal cases? - ✔✔Frye Standard What is the name of the standard Linux command that can be used to create bit-stream images? - ✔✔dd During the course of an investigation, you locate evidence that may prove the innocence of the suspect of the investigation. You must maintain an unbiased opinion and be objective in your entire fact finding process, therefore you report this evidence. This type of evidence is known as: - ✔✔Exculpatory evidence In what circumstance would an expert witness be allowed to state an opinion? - ✔✔C. the opinion, inferences, or conclusions depend on special knowledge, skill, or training not within the ordinary experience of lay jurors Which of following refers to the location of data that might still exist in a cluster even though the original file has been overwritten by another file? - ✔✔B. Slack space To make sure the evidence you recover and analyze with computer forensics software can be admitted in court, you must test and validate the software. What group is actively providing tools and creating procedures for testing and validating computer forensics software? - ✔✔National Institute of Standards and Technology (NIST) What does "message repudiation" refer to in the context De of e-mail investigations? - ✔✔Message repudiation means a sender can claim they did not actually send a particular message Which of the following BEST defines the term e-discovery? - ✔✔D. A process of producing electronically stored information for use as evidence. Which of the following file systems is most closely associated with the Mac OS? - ✔✔A. HFS+ of An investigator uses a process comparing monitored events to a specific attack model to determine whether or not the event qualifies as an intrusion. What is this called? process - ✔✔A. Signature-based detection When obtaining a search warrant it is important to - ✔✔C. Particularly describe the place to be searched and particularly describe the items to be seized One technique for hiding information is to change the file extension from the correct one to one that Dennis Thibo might not be noticed by an investigator, such as changing a .jpg extension to a .doc extension so that a picture file appears to be a document. What can an investigator examine to verify that a file has the correct extension? - ✔✔B. the file header When investigating a Windows system, it is important to v [Show More]
Last updated: 1 year ago
Preview 1 out of 9 pages
Instant download
Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Dec 15, 2022
Number of pages
9
Written in
Additional information
This document has been written for:
Uploaded
Dec 15, 2022
Downloads
0
Views
61

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)


En.png)

 2022.png)



.png)

