Business > QUESTIONS & ANSWERS > Introduction to Cryptography - C839 - ECES EC-Council Certified Encryption Specialist Practice Exam (All)
Introduction to Cryptography - C839 - ECES EC-Council Certified Encryption Specialist Practice Exam Already Passed
Document Content and Description Below
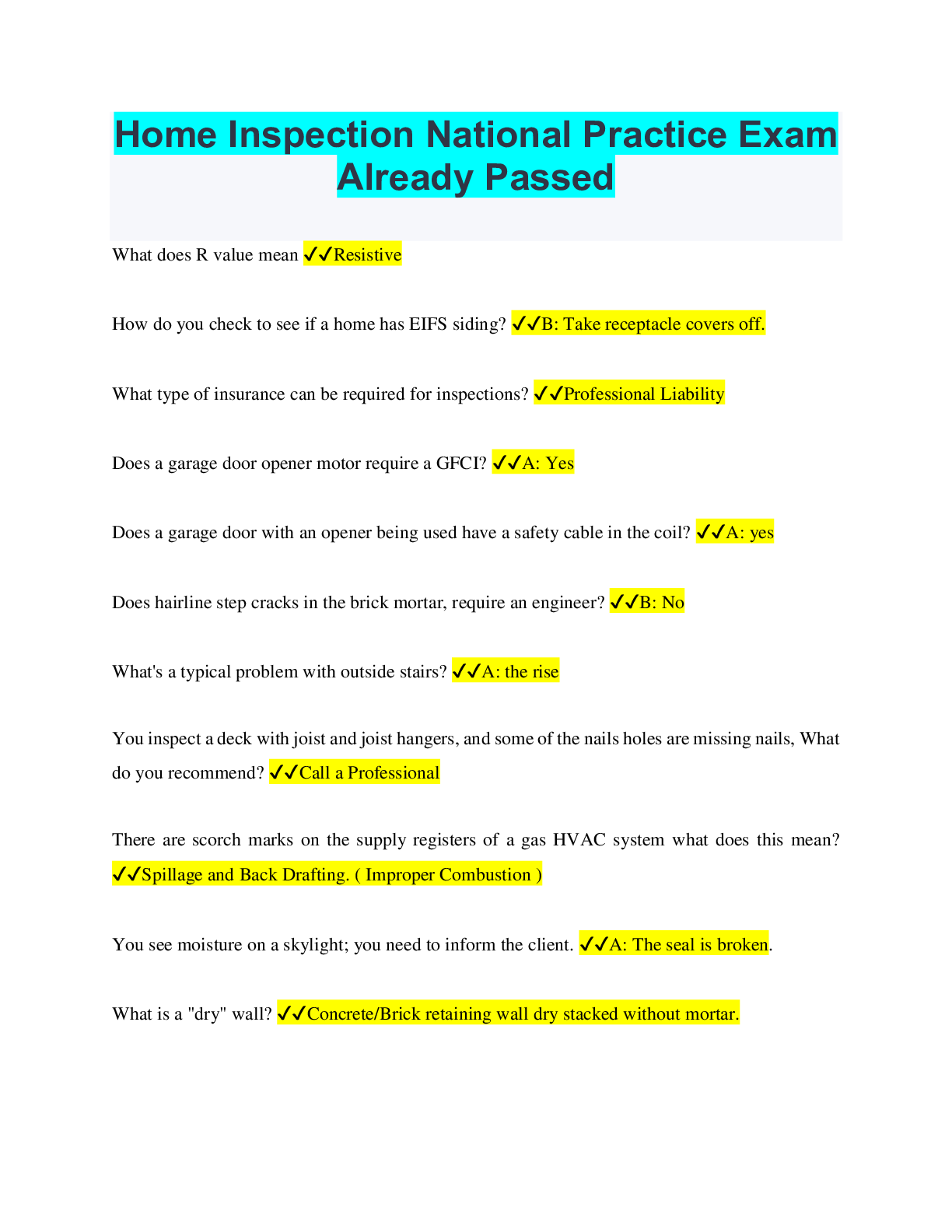
Introduction to Cryptography - C839 - ECES EC-Council Certified Encryption Specialist Practice Exam Already Passed 1. How did the ATBASH cipher work? ✔✔By substituting each letter for the lette... r from the opposite end of the alphabet (i.e. Abecomes Z, B becomes Y, etc.) 2. DES has a key space of what? ✔✔2^56 3. Which of the following are valid key sizes for AES (choose three)? ✔✔c. 128 d. 192 e. 256 4. Which of the following algorithms uses three different keys to encrypt the plain text? ✔✔3DES Triple Data Encryption System 5. Which of the following is a block cipher? ✔✔AES The Advanced Encryption Standard (AES) is a symmetric-key block cipher algorithm and U.S. government standard for secure and classified data encryption and decryption. 6. Which of the following is a type of encryption that has two different keys. One key can encrypt the message and the other key can only decrypt it? ✔✔Asymmetric 7. Which of the following is an asymmetric cipher? ✔✔RSA The acronym stands for Rivest, Shamir, and Adelman, the inventors of the technique. The RSA algorithm is based on the fact that there is *no efficient way to factor very large numbers.* 8. A cipher is defined as what ✔✔The algorithm(s) needed to encrypt and decrypt a message 9. Which of the following is not an asymmetric system? ✔✔AES The Advanced Encryption Standard (AES) is a symmetric-key block cipher algorithm and U.S. government standard for secure and classified data encryption and decryption. 10. John is going to use RSA to encrypt a message to Joan. What *key* should he use? ✔✔Joan's public key 11. What advantage do symmetric algorithms have over asymmetric algorithms ✔✔Symmetric algorithms are faster than Asymmetric algorithms 12. Which of the following is generally true about key sizes? ✔✔Larger key sizes increase security 13. A ____ is a function is not reversible. ✔✔Hash 14. Which of the following is a protocol for exchanging keys? ✔✔*DH* Diffie-Hellman is a way of *generating a shared secret between two people* in such a way that the secret can't be seen by observing the communication. That's an important distinction: You're not sharing information during the key exchange, *you're creating a key together.* 15. Which of the following would be the fastest process? ✔✔AES The Advanced Encryption Standard (AES) is a symmetric-key block cipher algorithm and U.S. government standard for secure and classified data encryption and decryption. 16. Which of the following would be the *weakest encryption* algorithm? ✔✔DES Data Encryption Standard 17. What is the largest key size that AES can use? ✔✔256 18. What are a few different *key exchange protocols?* ✔✔*MED* DH - Diffie-Hellman MQV - Menezes-Qu-Vanstone is an *authenticated protocol* for key agreement *based on the Diffie-Hellman* scheme ECDH - ECDH is a *variant* of the Diffie-Hellman algorithm for *elliptic curves* AES *is not* a key exchange protocol; it is a Symmetric Block Cipher 19. Which of the following is a key exchange protocol? ✔✔MQV MQV (Menezes-Qu-Vanstone) is an authenticated protocol for key agreement based on the Diffie-Hellman scheme. Like other authenticated Diffie-Hellman schemes, MQV provides protection against an active attacker. 20. Which of the following encryption algorithms relies on the *inability to factor large prime numbers?* ✔✔*RSA* The acronym stands for Rivest, Shamir, and Adelman, the inventors of the technique. The RSA algorithm is based on the fact that there is *no efficient way to factor very large numbers.* 21. Using substitution without transposition leads to what *weakness?* ✔✔Letter/word frequency is maintained 22. What algorithm does the *clipper chip* use? ✔✔Skipjack *Remember CLIPskip* 23. What size key does Skipjack use? ✔✔80 bit 24. What size block does Skipjack use? ✔✔64 25. With *E*lectronic *C*ode*B*ook (ECB) what happens ✔✔The *message* is divided into blocks and *each block is encrypted separately.* This is the most basic mode for symmetric encryption. *Think of the OSI 7-Layer Model, TRANSPORT Layer under TCP* 26. Which algorithm implements an *Unbalanced Feistel* cipher? ✔✔Skipjack 27. With Cipher-*block chaining* (*CBC*) what happens? ✔✔Each block of plaintext is *XOR*'d *with* the *previous ciphertext block BEFORE being encrypted* *XOR* a.k.a. (e*X*clusive *OR*). A Boolean logic operation that is widely used in cryptography as well as in generating parity bits for *error checking and fault tolerance.* XOR compares two input bits and generates one output bit. 28. What happens with *C*ipher *F*eed*B*ack (*CFB*)? ✔✔The *ciphertext block is ENCRYPTED then* the ciphertext produced is *XOR*'d back *with* the *plaintext* to produce the current ciphertext block. *1 - Ciphertext block is Encrypted* *2 - Ciphertext XOR/error check with Plaintext* *3 - Current Ciphertext Block produced* 29. What does Output feedback (*OFB*) do? ✔✔A *block cipher is converted into a stream cipher* by generating a key-stream blocks, which are then XORed with the plaintext blocks to get the ciphertext 30. Which of the following modes cannot be used to *turn a block cipher into a stream cipher?* ✔✔CTR OFB CTR is a chaining mode for symmetric block encryption or decryption. Messages are divideded into blocks, and the cipher operation takes place on each block using the secret key and a unique counter block Output feedback (OFB) is a mode of operation for a block cipher. 31. What is an IV? ✔✔A *fixed size random stream that is added to a block cipher* to increase randomeness. 32. A number that is used only one time, then discarded is called what? ✔✔Nonce 33. What is the *largest key size* that *RC4* can use? ✔✔256 bits 34. What is the basis for the *FI*SH algorithm? ✔✔The Lagged *Fi*bonacci generator 35. Which of the following is *required* for a hash? ✔✔*VLI & FLO* a. Variable length input, fixed length output b. Few collisions d. Not reversible 36. Which of the following is used to *encrypt email AND create digital signatures?* ✔✔RSA The acronym stands for Rivest, Shamir, and Adelman, the inventors of the technique. The RSA algorithm is based on the fact that there is no efficient way to factor very large numbers. 37. Bob's password is hashed, and so is John's. Even though they used different passwords, the *hash is the same.* What is this called? ✔✔A collision 38. In relationship to hashing, the term ____ refers to *random bits* that are used *as one of the inputs* to the hash. Essentially the is intermixed with the message that is to be hashed. ✔✔Salt 39. This is a *128-bit* hash that is specified by RFC 1321. It was *designed* by Ron Rivest in 1991 *to replace an earlier hash* function. ✔✔MD5 MD5 (*M*essage-*D*igest algorithm *5*) is a widely used cryptographic hash function with a 128-bit hash value. 40. This hash function *uses 512-bit blocks* and implements preset constants that change after each repetition. *Each block is hashed into a 256-bit block* through four branches that divides each 512 block into *sixteen 32-bit* words that are further encrypted and rearranged ✔✔FORK256 41. Which of the following is an *asymmetric* algorithm that was first publicly described in *1977?* ✔✔*RSA* The acronym stands for Rivest, Shamir, and Adelman, the inventors of the technique. The RSA algorithm is based on the fact that there is no efficient way to factor very large numbers. 42. Which of the following *equations* describes the encryption process for *RSA?* ✔✔*M^e % n* M to the "e" power % n 43. Which of the following is an *asymmetric* algorithm related to the *equation* *y2= x3+ Ax + B?* ✔✔Elliptic Curve *Remember this is a type of DH; more known as ECDH* 44. Which of the following *asymmetric* algorithms is described by *U.S. Patent* 5,231,668 and *FIPS* ✔✔*DSA* DSA stands for *Digital Signature Algorithm* - and is specifically designed to produce digital signatures, *not perform encryption* 45. Which of the following is the *standard for digital certificates?* ✔✔X.509 46. Rather than look in a list, one can use a *protocol* to find *revoked certificates.* What protocol is that? ✔✔OCSP = *Online Certificate Status Protocol* 47. What must occur in order for a *cipher* to be considered *broken?* ✔✔You must find a method that is *more efficient* than Brute force. 48. __________ cryptography uses *one key to encrypt* a message and a *different key to decrypt* it. ✔✔Asymmetric 49. If the *round function* is a cryptographically secure pseudorandom function, then _____ rounds is sufficient to make the block cipher a *pseudorandom permutation.* ✔✔3 50. If the *round function* is a cryptographically secure pseudorandom function, then ____ rounds is sufficient to make it a *STRONG* pseudorandom permutation. ✔✔4 [Show More]
Last updated: 11 months ago
Preview 1 out of 12 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
We Accept:

Reviews( 0 )
$10.00
Document information
Connected school, study & course
About the document
Uploaded On
Jul 21, 2023
Number of pages
12
Written in
Additional information
This document has been written for:
Uploaded
Jul 21, 2023
Downloads
0
Views
110

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)

