Information Technology > QUESTIONS & ANSWERS > WGU C795 NOC REPORTING TEMPLATE LATEST UPDATED 2022 ALREADY PASSED (All)
WGU C795 NOC REPORTING TEMPLATE LATEST UPDATED 2022 ALREADY PASSED
Document Content and Description Below
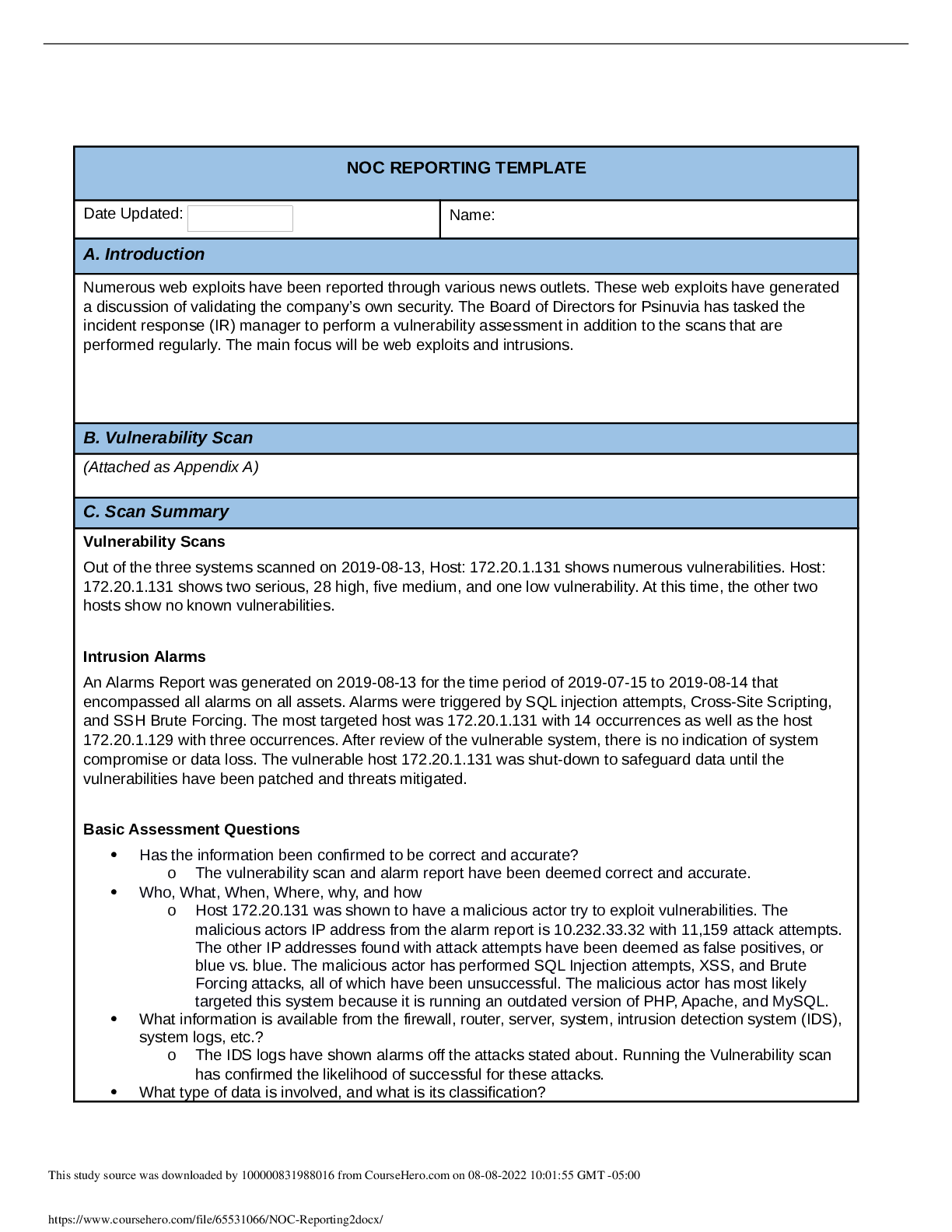
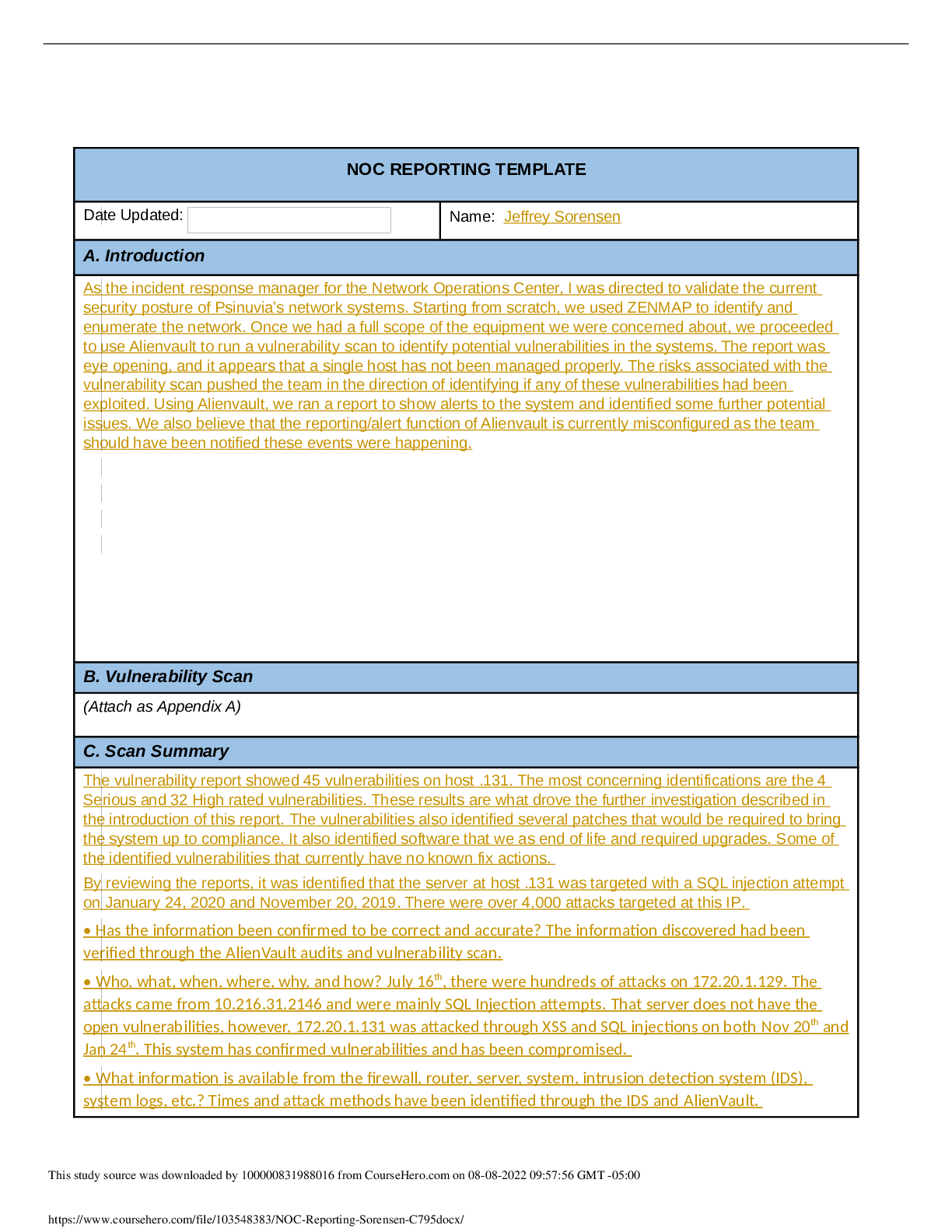
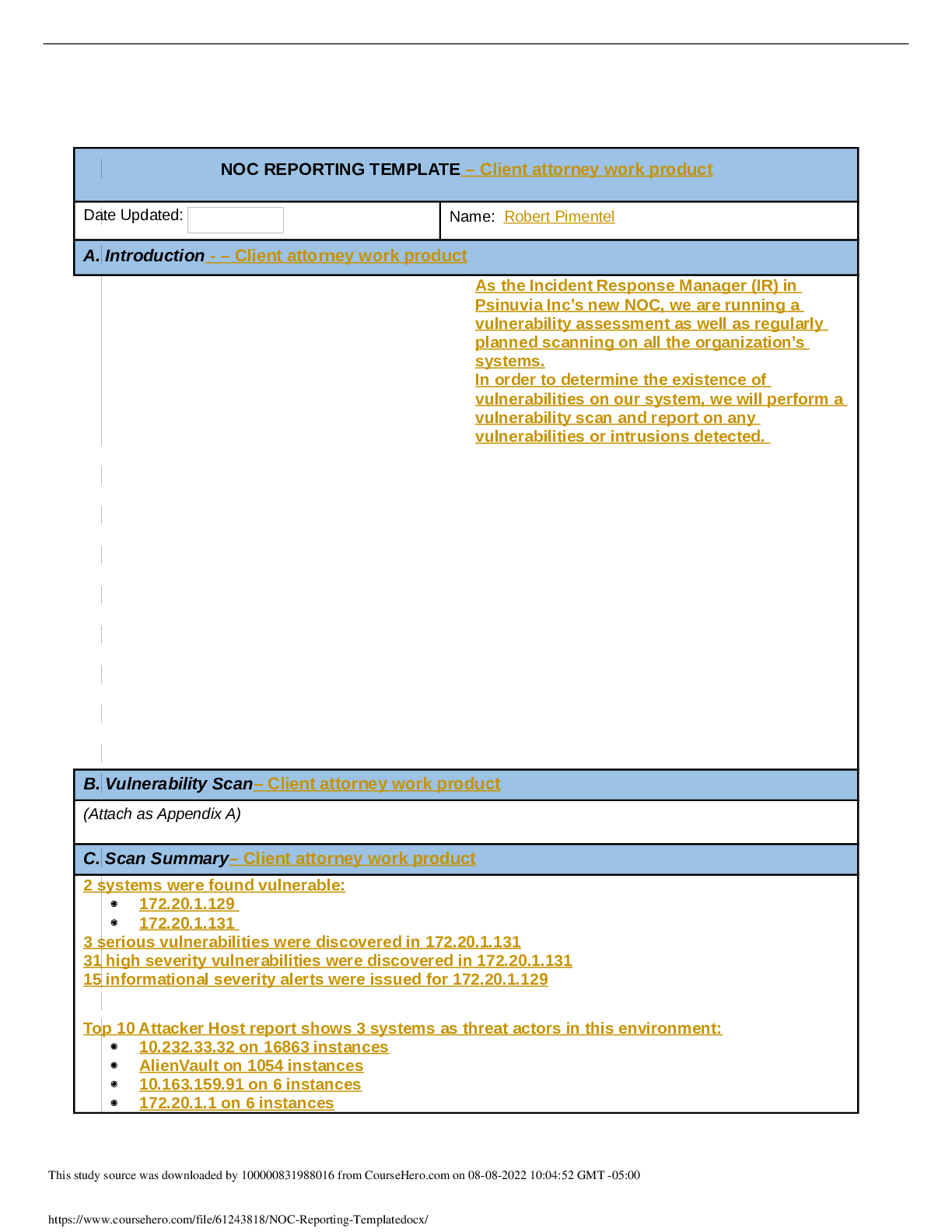
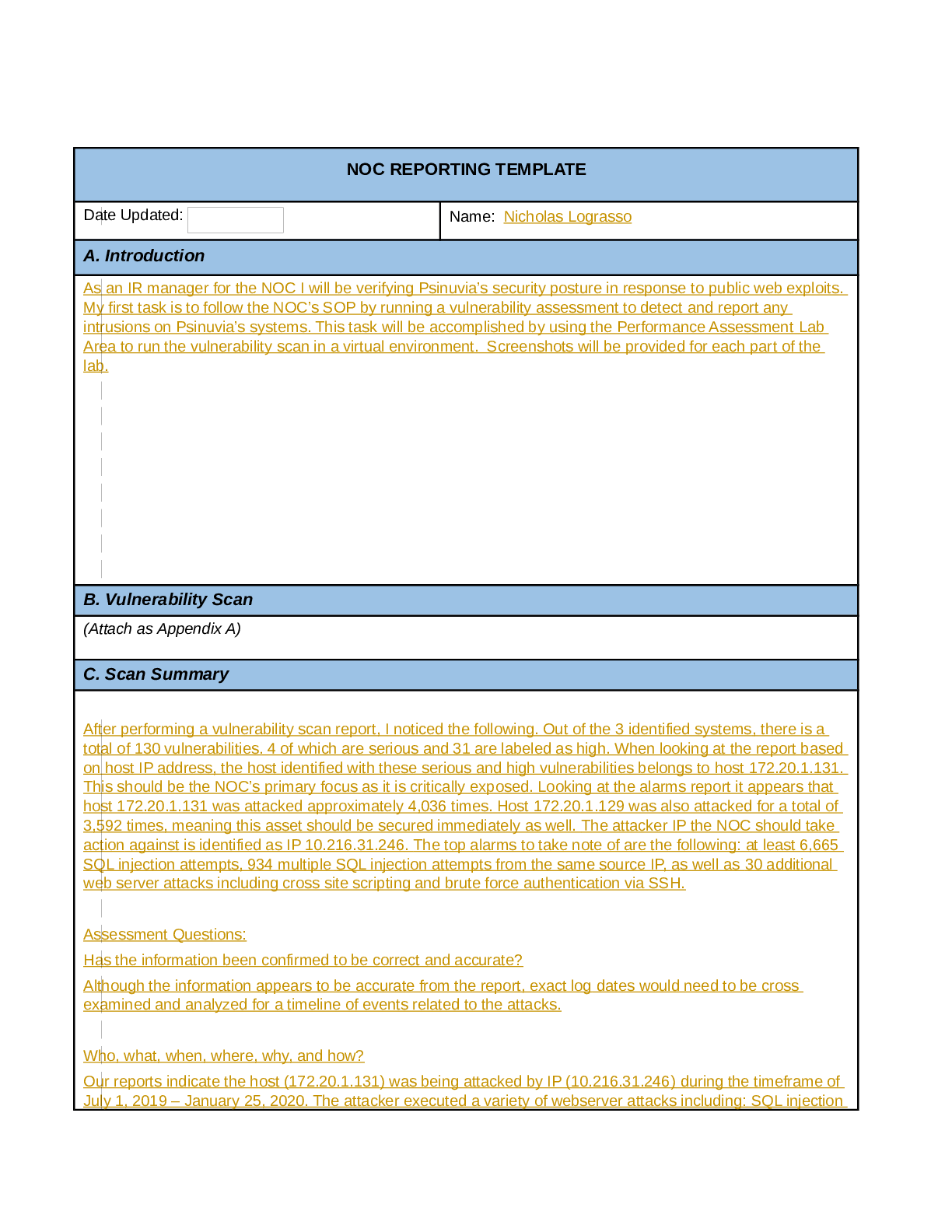
NOC REPORTING TEMPLATE Date Updated: Name: Michael Roberts A. Introduction The Psinuvua Board of Directors have recently requested that scans be conducted on the internal systems as there had been ... multiple media reports through news media outlets that showed web exploits being used on other businesses. As a result, the security of the internal network is being assessed in addition to the routine scans. The task has been delegated to the incident response manager and team. While conducting the scan and alert verification from the IDS regarding the 172.20.1.0/24 subnet, it was identified that there was a host (172.20.1.131) that was being attacked via a SQL injection due to the exposure of a backend database through an Apache Web Server. After examining the device, it was determined that there were multiple attempts to exploit the database through SQL Injection, Cross-Site Script (XSS) attacks, and exploitation of the webserver (Apache). B. Vulnerability Scan (Attach as Appendix A) C. Scan Summary 1. Has the information been confirmed to be correct and accurate? a. SQL injection occurred on the host 172.20.1.131 and was confirmed with the vulnerability scanner and Zenmap, and Alien Vault OSSIM outputs 2. Who, what, when, where, why, and how? a. SQL Injections against the database connected to a PHP web-application, via unfiltered/unmodified statements being sent directly to the database 3. What information is available from the firewall, router, server, system, intrusion detection system (IDS), system logs, etc.? a. No additional information outside of Zenmap, Alien Vault OSSIM, and the vulnerability scan has been provided. The results from the IDS are part of the vulnerability assessment integrated with Alien Vault OSSIM. 4. What type of data is involved, and what is its classification? a. The data involved is from the database, using SQL commands. The data structure is not known, and the data contained within it is assumed Business related, meaning it would be classified as sensitive information. 5. Are there obscenities, child pornography, or confrontational data? a. The data appears to be business-related, so the assumption would be no. However, there is no schematic or data shown that can verify it. This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 09:52:06 GMT -05:00 https://www.coursehero.com/file/78720075/NOC-Report-MROBPAC795docx/ 6. Is there criminal activity? a. There is no precise data about whether the SQL injections successfully extracting information from the database, only that it was vulnerable and may have been used. No clear indication of criminality can be determined, but it likely would be assumed during the process to ensure the chain of custody was intact if any evidence of data theft had occurred. 7. Is the data protected by an encryption solution? a. No. The system currently uses a plaintext HTTP connection to the web application and from the web application to the database. 8. What is the magnitude of the systems being impacted? a. The database controls all the critical data for the web application and contains restricted business data, which would make the breach a high magnitude. 9. Is the event still in progress? a. Not enough information is present to determine if the attack is ongoing, only that the attacks could be persisting without being noticed. 10. Has preliminary containment been performed (i.e., disable the account, reset the password, remove remote access, isolate device in the segregated segment)? a. The scan results did not show specific accounts that could be disabled or removed in order to prevent this attack. However, a few lines of code and some patching of software would remove the vulnerability. 11. What is the estimated value of the impacted data and systems? 12. a. There is not enough information to determine the value of the information in the database or what was potentially taken if any. Regardless of monetary cost, there will be a reputational cost to any client or enduser due to the breach. b. The overall result of the scan identified that a single host (172.20.1.131) was being targeted with XSS, SQL, and Webserver (Apache) attacks, with the focus being on SQL injection. It also identified that the host was a web server application using unencrypted communications for public and internal connections. Vulnerability Scans: As demonstrated in the image below, the host 172.20.1.131 was the only host that was identified as having vulnerabilities, but the others had information that may require additional attention This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 09:52:06 GMT -05:00 https://www.coursehero.com/file/78720075/NOC-Report-MROBPAC795docx/ Alarm Reports: Alarms were triggered by SQL injection attempts, Cross-Site Scripting, and SSH Brute Forcing with the primary target being 172.20.1.131. There was 2,282 alerts that triggered on the host 172.20.1.131: This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 09:52:06 GMT -05:00 https://www.coursehero.com/file/78720075/NOC-Report-MROBPAC795docx/ The alerts were based on the attacks shown below: D. Detailed Analysis The steps taken to identify exploited systems and data are as follows: 1. Initially run a Zenmap scan of all the devices 2. Then executed a vulnerability scan with Alien Vault OSSIM tool. This enumerated all assets and provided a report that is attached in Appendix A. 3. Examined the reports, identifying the main vulnerability was a SQL injection with 2,335 occurrences This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 09:52:06 GMT -05:00 https://www.coursehero.com/file/78720075/NOC-Report-MROBPAC795docx/ 4. 5. The report identified SQL injection as a large portion of the vulnerabilities; it became the response's primary focus and likely largest attack surface that could be closed. 6. Upon further investigation, the determination that the device responsible for the majority of the vulnerabilities was 172.20.1.131, as demonstrated below 7. 8. This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 09:52:06 GMT -05:00 https://www.coursehero.com/file/78720075/NOC-Report-MROBPAC795docx/ 9. Based on the report from the vulnerability scan, the Zenmap output, and the Alert based information, it can be determined that the vulnerabilities exist on machine 172.20.1.13 [Show More]
Last updated: 1 year ago
Preview 1 out of 9 pages
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Aug 08, 2022
Number of pages
9
Written in
Additional information
This document has been written for:
Uploaded
Aug 08, 2022
Downloads
0
Views
151

.png)
.png)
.png)
.png)
.png)
.png)






.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
 (1).png)
.png)
.png)