Information Technology > QUESTIONS & ANSWERS > WGU C795 NOC REPORTING TEMPLATE LATEST 2022 RATED A (All)
WGU C795 NOC REPORTING TEMPLATE LATEST 2022 RATED A
Document Content and Description Below
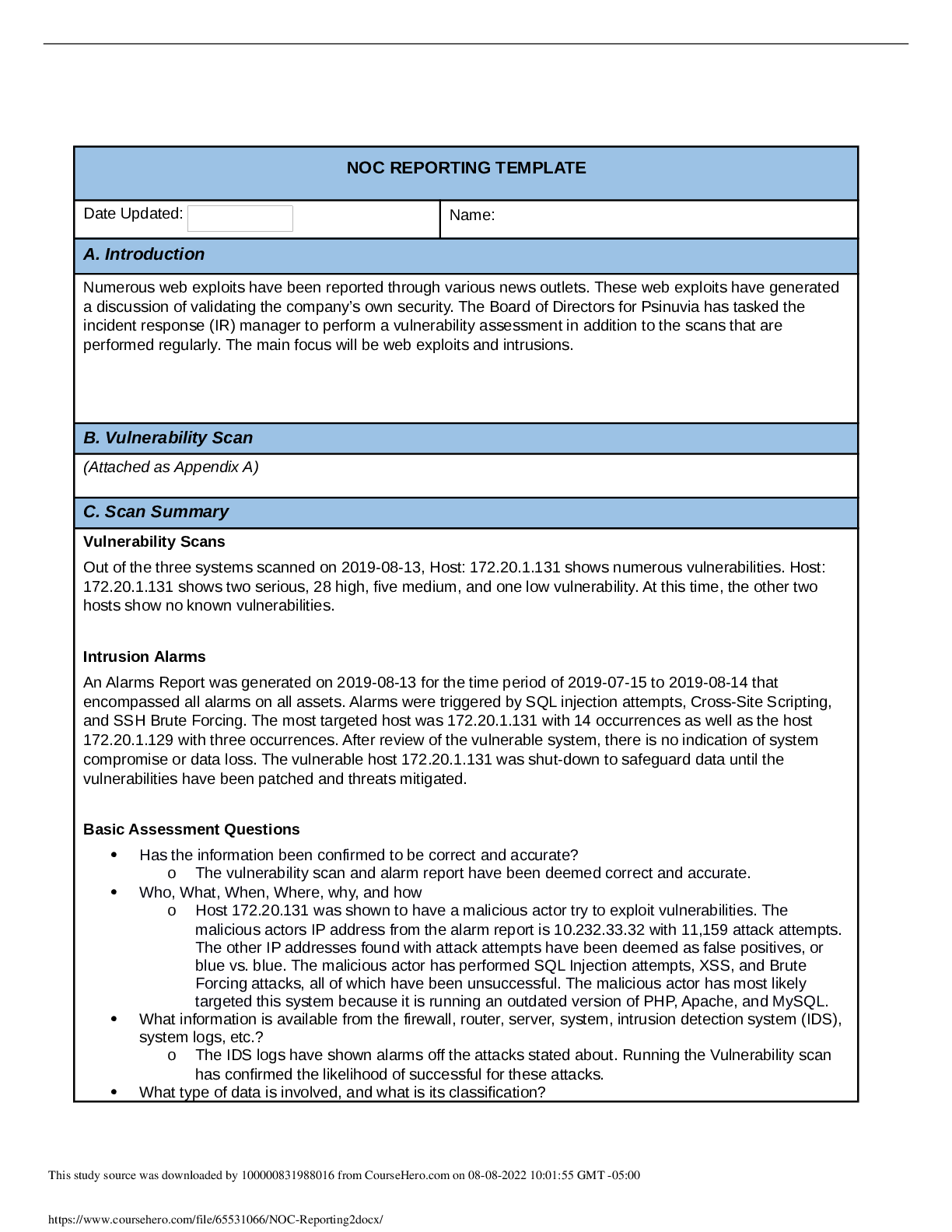
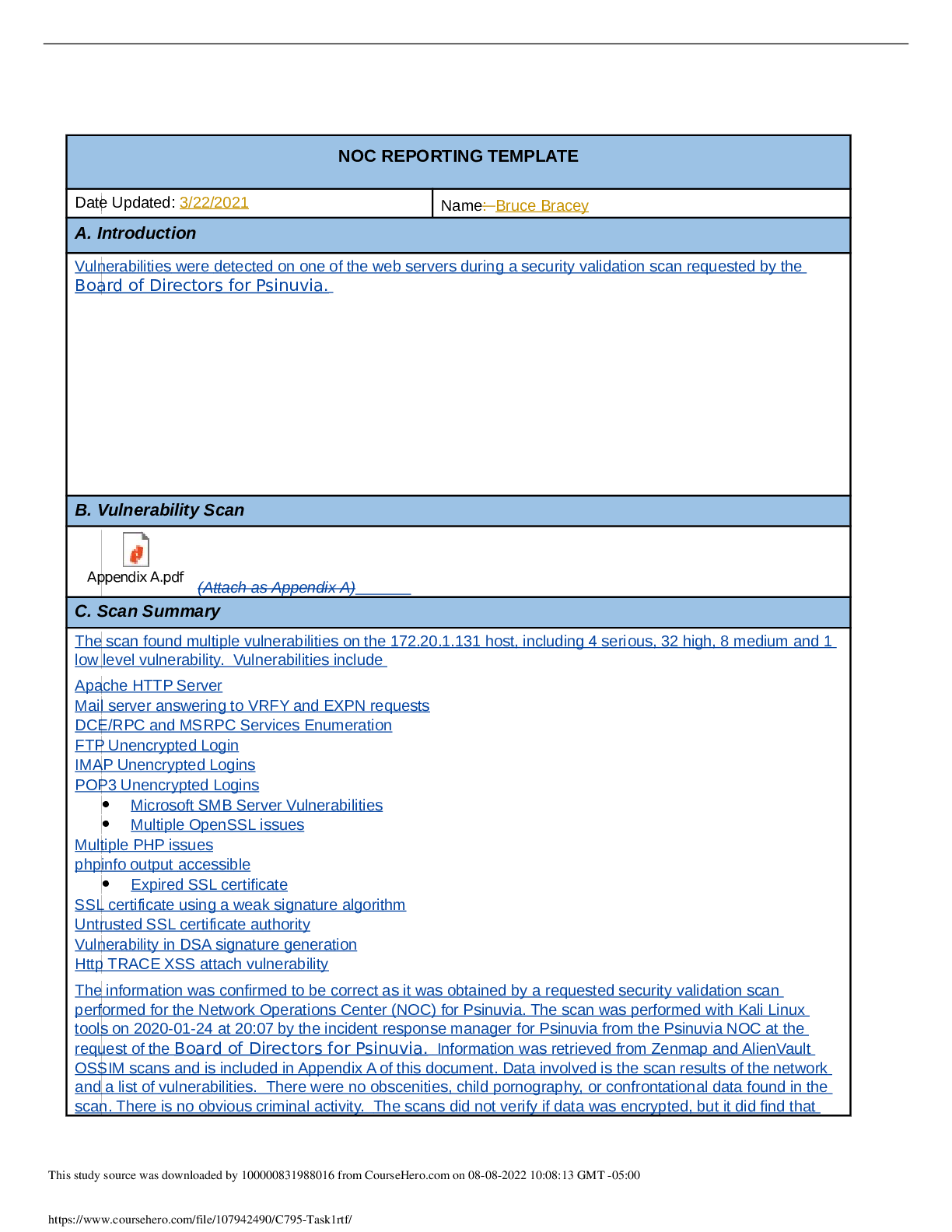
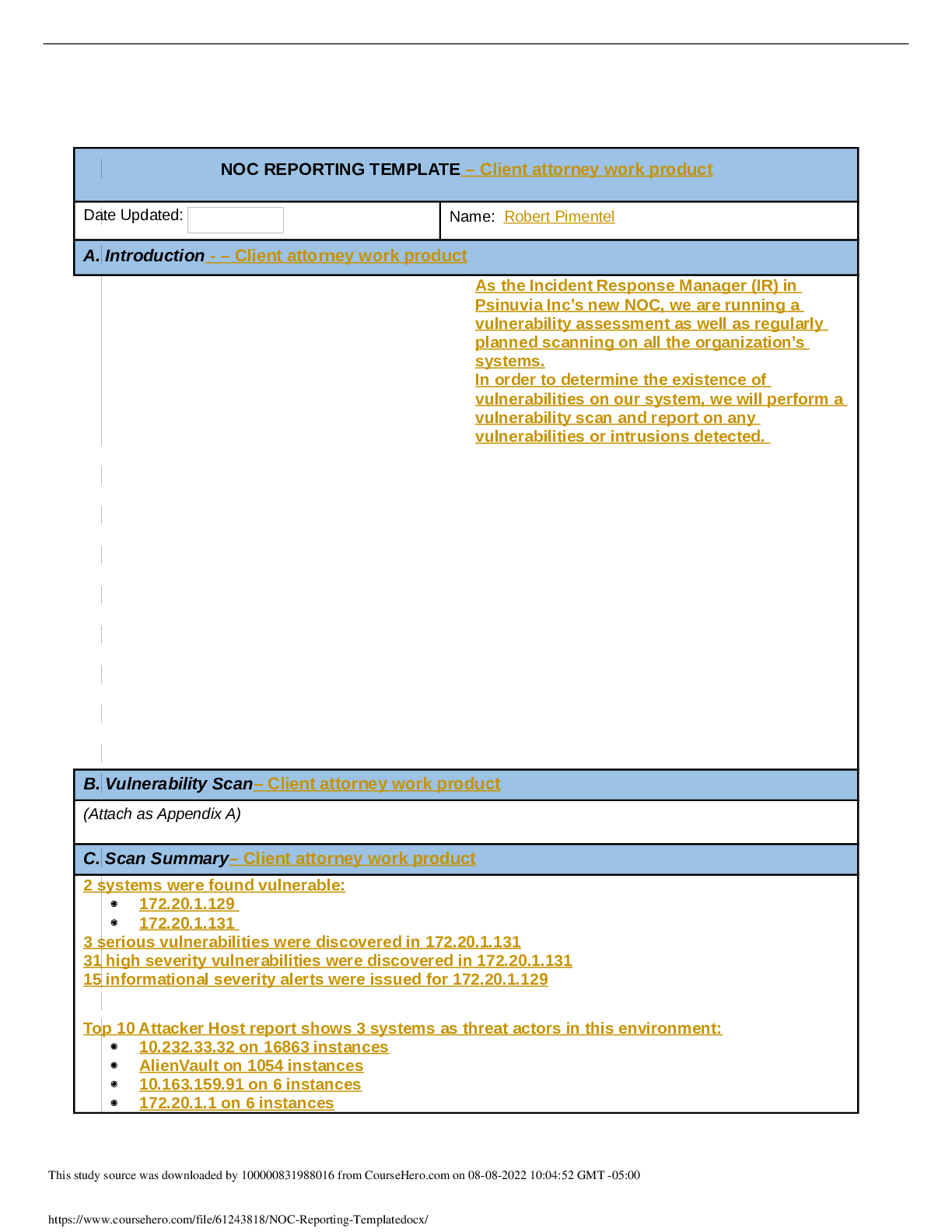
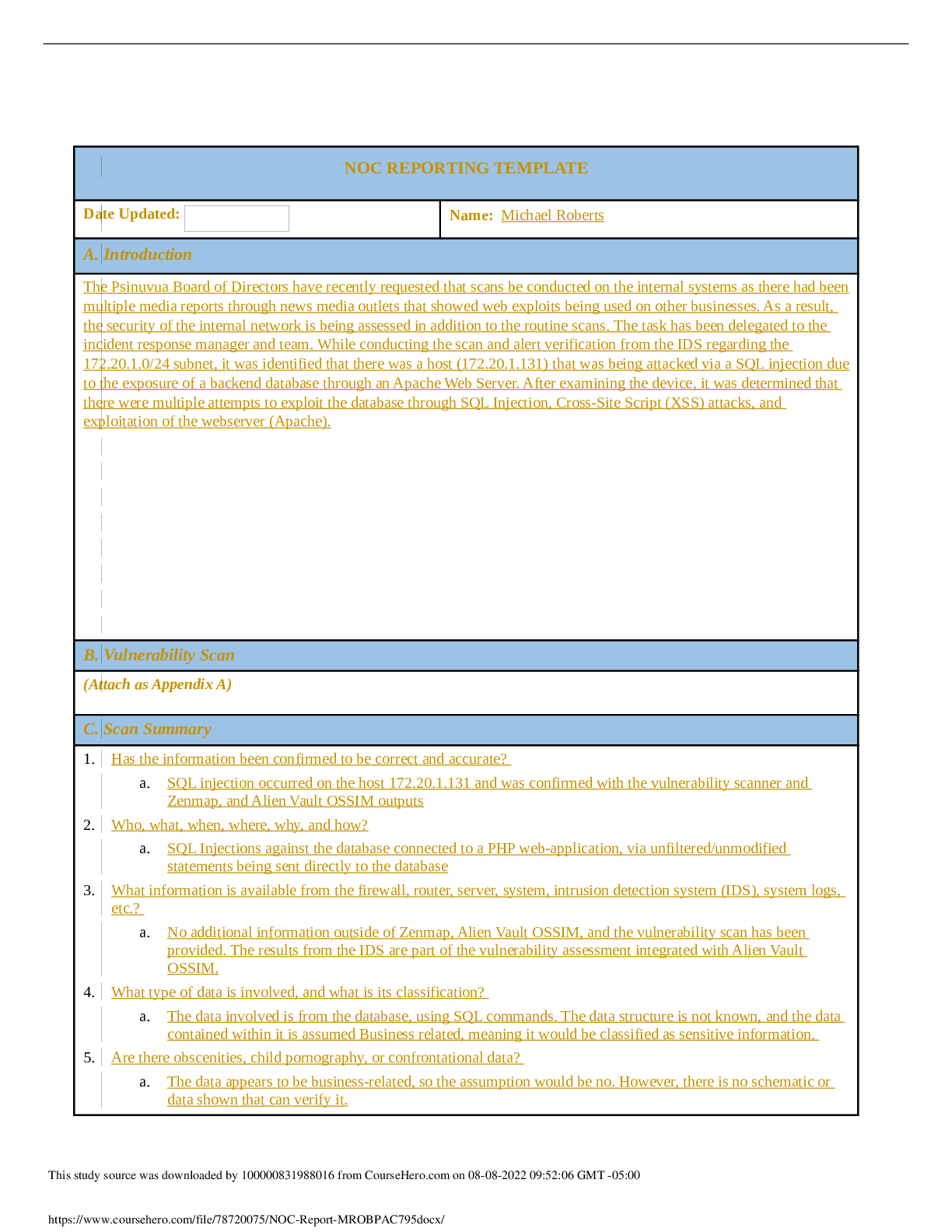
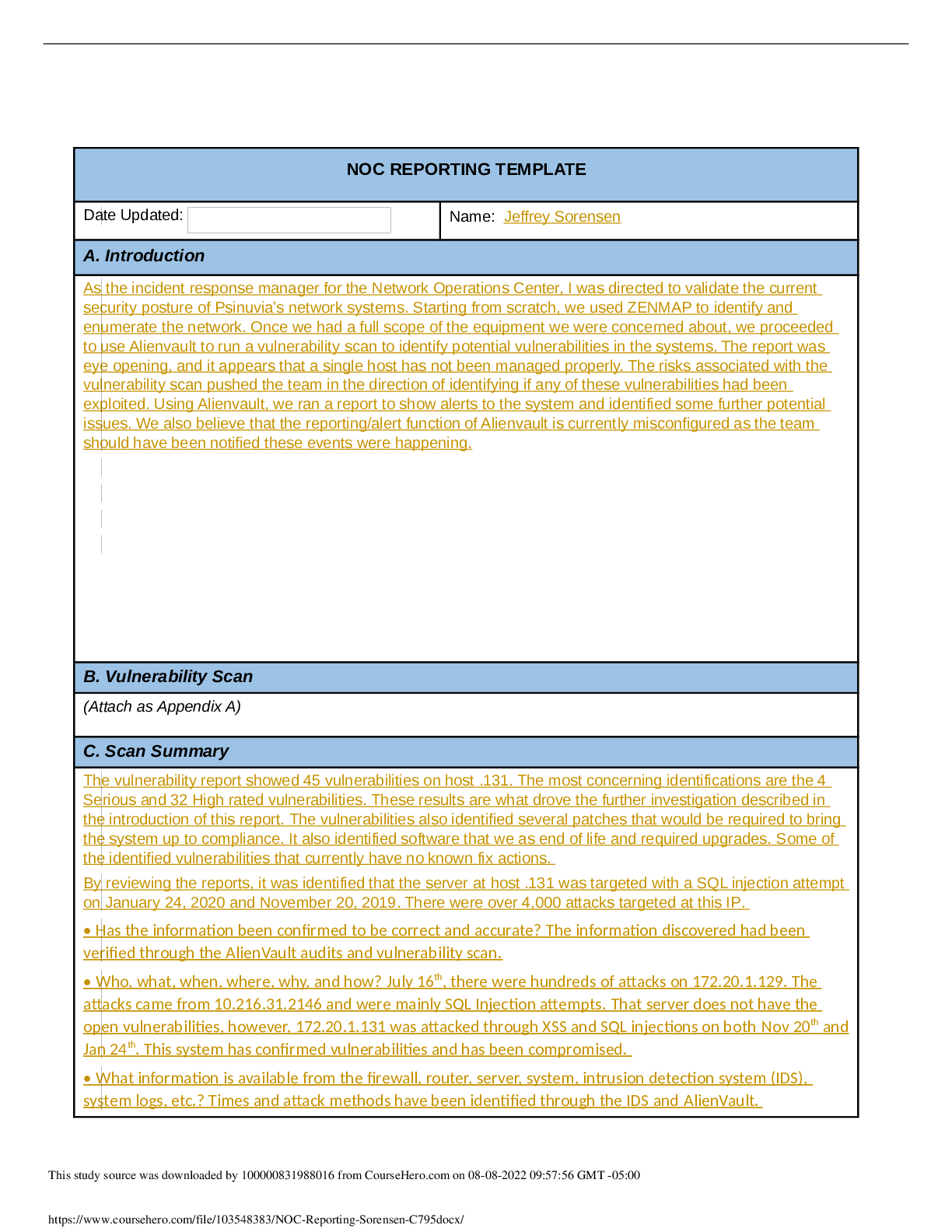
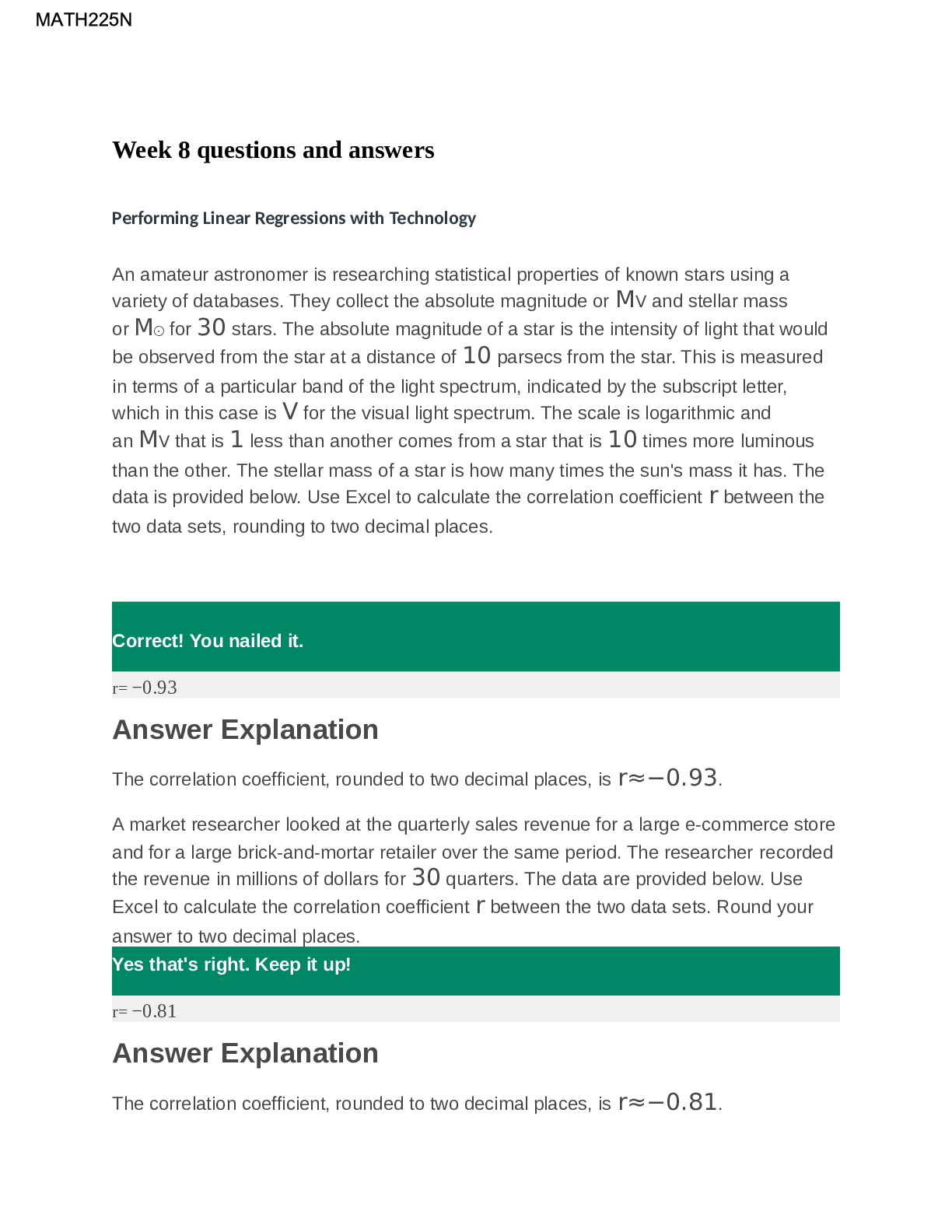
NOC REPORTING TEMPLATE Date Updated: Name: A. Introduction Numerous web exploits have been reported through various news outlets. These web exploits have generated a discussion of validating the c... ompany’s own security. The Board of Directors for Psinuvia has tasked the incident response (IR) manager to perform a vulnerability assessment in addition to the scans that are performed regularly. The main focus will be web exploits and intrusions. B. Vulnerability Scan (Attached as Appendix A) C. Scan Summary Vulnerability Scans Out of the three systems scanned on 2019-08-13, Host: 172.20.1.131 shows numerous vulnerabilities. Host: 172.20.1.131 shows two serious, 28 high, five medium, and one low vulnerability. At this time, the other two hosts show no known vulnerabilities. Intrusion Alarms An Alarms Report was generated on 2019-08-13 for the time period of 2019-07-15 to 2019-08-14 that encompassed all alarms on all assets. Alarms were triggered by SQL injection attempts, Cross-Site Scripting, and SSH Brute Forcing. The most targeted host was 172.20.1.131 with 14 occurrences as well as the host 172.20.1.129 with three occurrences. After review of the vulnerable system, there is no indication of system compromise or data loss. The vulnerable host 172.20.1.131 was shut-down to safeguard data until the vulnerabilities have been patched and threats mitigated. Basic Assessment Questions Has the information been confirmed to be correct and accurate? o The vulnerability scan and alarm report have been deemed correct and accurate. Who, What, When, Where, why, and how o Host 172.20.131 was shown to have a malicious actor try to exploit vulnerabilities. The malicious actors IP address from the alarm report is 10.232.33.32 with 11,159 attack attempts. The other IP addresses found with attack attempts have been deemed as false positives, or blue vs. blue. The malicious actor has performed SQL Injection attempts, XSS, and Brute Forcing attacks, all of which have been unsuccessful. The malicious actor has most likely targeted this system because it is running an outdated version of PHP, Apache, and MySQL. What information is available from the firewall, router, server, system, intrusion detection system (IDS), system logs, etc.? o The IDS logs have shown alarms off the attacks stated about. Running the Vulnerability scan has confirmed the likelihood of successful for these attacks. What type of data is involved, and what is its classification? This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 10:01:55 GMT -05:00 https://www.coursehero.com/file/65531066/NOC-Reporting2docx/ o Given that the host that was attacked, 172.20.1.131, is a web server running PHP, MySQL, and Apache it can be determined that the data is sensitive customer and company data. Personal Identifiable Information can also be found within the web servers databases. Are there obscenities, child pornography, or confrontational data? o N/A Is there criminal activity o N/A Is the data protected by an encryption solution? o No What is the magnitude of the systems being impacted? o Is the system were to go down, this would affect the rest of the company because of the importance of the databases and nature of web servers. If an attacker were to gain access, sensitive customer and company data and PII would be left exposed. Is the event still in progress? o No Has preliminary containment been performed? o Containment has been performed by force shutting down the vulnerable host through SSH console. What is the estimated value of the impacted data and systems? o Due to the data that’s on the vulnerable host and the possibility of using the host as a pivot into the rest of Psinuvia’s systems the impact is severe. The estimated cost of the systems impacted $200 million. D. Detailed Analysis After performing the vulnerability scan and generating an alarms report it was determined that host 172.20.1.131 was the victim of several attempted attacks. This host is a webserver running Apache and MYSQL that also utilizes PHP. Given the scope of Psinuvia, it can be presumed that the database encompasses sensitive user data including PHI and company data with no encryption at-rest. Figure 1 Figure 1 - The image above shows the breakdown of each host within the system along with the criticality of vulnerabilities. This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 10:01:55 GMT -05:00 https://www.coursehero.com/file/65531066/NOC-Reporting2docx/ According to the vulnerability scan, it was indicated that the two serious risks were PHP versions at the end of life on ports 80 and 443. With PHP being end-of-life, this opens up a sizeable attack vector to the system. Several other various vulnerabilities were also found with the version of the Apache webserver that is running. It was also discovered that there are configuration vulnerabilities within the webserver that would allow attackers to use a form of Cross-Site Tracing, i.e. TRACE and TRACK methods are enabled. Figure 2 Figure 2 – Shows the type of attacks and the number of occurences per attack according to the OSSIM logs. These attacks correspond with the vulnerabilities found in Appendix A. This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 10:01:55 GMT -05:00 https://www.coursehero.com/file/65531066/NOC-Reporting2docx/ Figure 3 Figure 3 – Currently installed versions of each of the services. These versions were taken from the XAMPP command line. The most recent downloadable versions are: MariaDB – 10.4, PHP – 7.3.11, and Apache – 2.4.41. Figure 4 Figure 4 – Shows the most prominent IP address (10.232.33.32) that the attacks came from. The other values are from false positives or blue vs. blue attacks according to the OSSIM logs. This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 10:01:55 GMT -05:00 https://www.coursehero.com/file/65531066/NOC-Reporting2docx/ Figure 5 Figure 5 – Show the evidence of attempted attacks and the number of occurrences towards the host 172.20.1.131 according to the OSSIM logs. E. Scan Response According to Psinuvia’s Incident Response Plan, this incident’s severity type is labeled as ‘High’ due to the unsuccessful attempts of compromising sensitive data. Also, a higher-than-normal level of intruder scanning and probing activity was noticed. The personnel to notify are the Chief Information Security Officer, Chief Technology Officer, the Legal Team, Security, and other management personnel. Initial response time should be four hours with a minimum of every two hours during restoration of services. F. Remediation When the vulnerable host was identified, the host machine was quarantined from the system network by performing a force shutdown via command console through SSH. A force-shutdown was performed because the host was found to have several serious and critical vulnerabilities. These vulnerabilities could be exploited and used as a pivot to gain access to the rest of the system. Since there were no signs of data-exfiltration or evidence of attacks gaining access into the system, according to NIST 800-61, Computer Incident Handling Guide, paragraph 3.3.1, the best course of action to take was to shut down the system and remove it from the network. The remediation of the vulnerable host will be solved through patch management and updating throughout the host’s lifecycle. Future updating and patch management is needed because this will mitigate potential known vulnerabilities from being exploited due to outdated systems. G. Recommendations Administrative Controls: Perform regular vulnerability scans; Technical Controls: Implement ACL Firewall Rule that allows SSH from This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 10:01:55 GMT -05:00 https://www.coursehero.com/file/65531066/NOC-Reporting2docx/ Implement patch management policy; Review/implement input validation on web applications; Admin IP and denies all others; Encrypt hosts that contain PII and sensitive customer/company data; Implement 2-Factor Authentication Install File Integrity Auditing Software Sources Cichonski, P., Miller, T., Grance, T., & Scarfone, K. Computer Security Incident Handling Guide, Computer Security Incident Handling Guide (2012). Gaithersburg, MD: U.S. Dept. of Commerce. This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 10:01:55 GMT -05:00 https://www.coursehero.com/file/65531066/NOC-Reporting2docx/ Powered by TCPDF (www.tcpdf.org) [Show More]
Last updated: 1 year ago
Preview 1 out of 6 pages
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Aug 08, 2022
Number of pages
6
Written in
Additional information
This document has been written for:
Uploaded
Aug 08, 2022
Downloads
1
Views
352

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)

.png)

.png)
.png)
.png)
.png)
.png)


.png)


.png)

.png)

