Information Technology > QUESTIONS & ANSWERS > WGU C795 NOC REPORTING TEMPLATE ALREADY PASSED (All)
WGU C795 NOC REPORTING TEMPLATE ALREADY PASSED
Document Content and Description Below
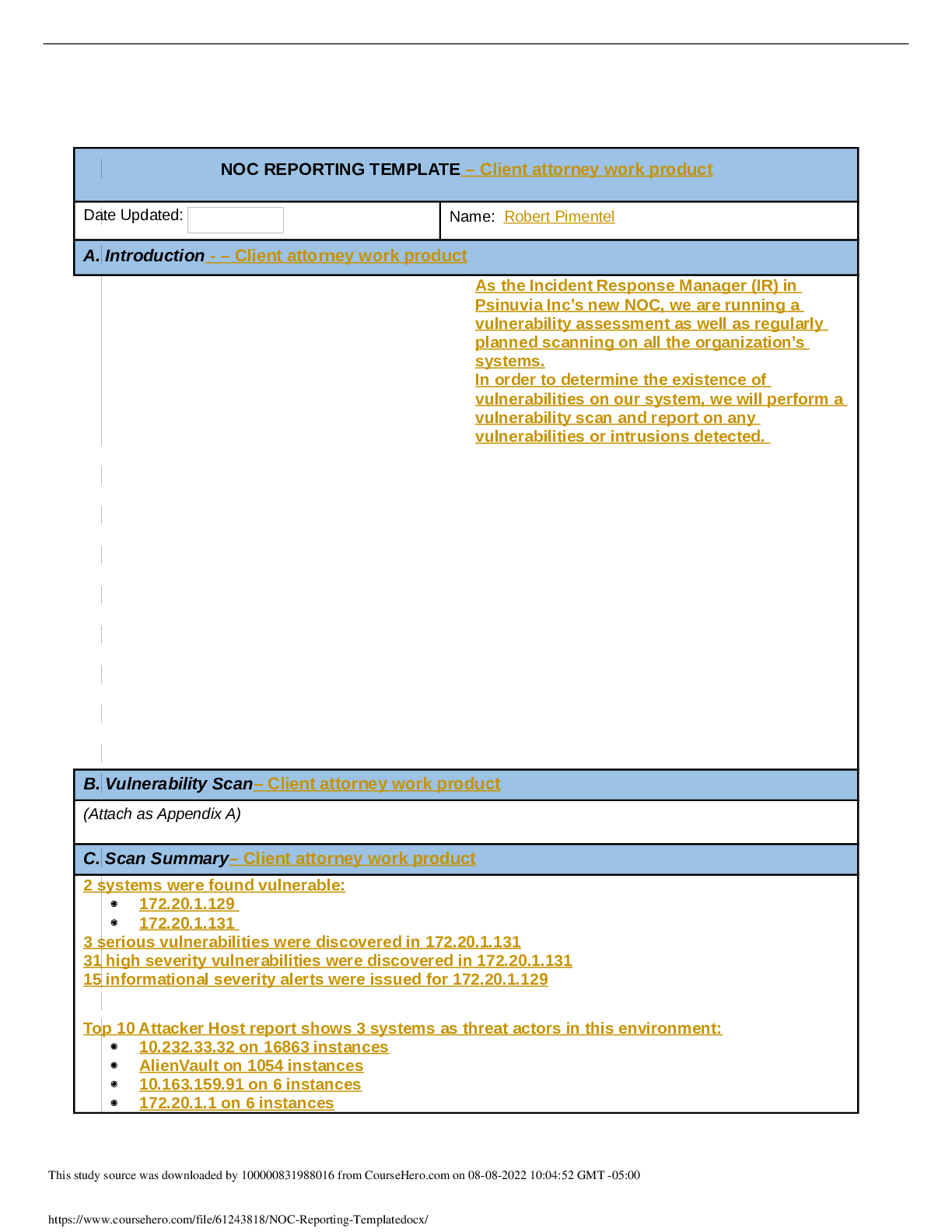
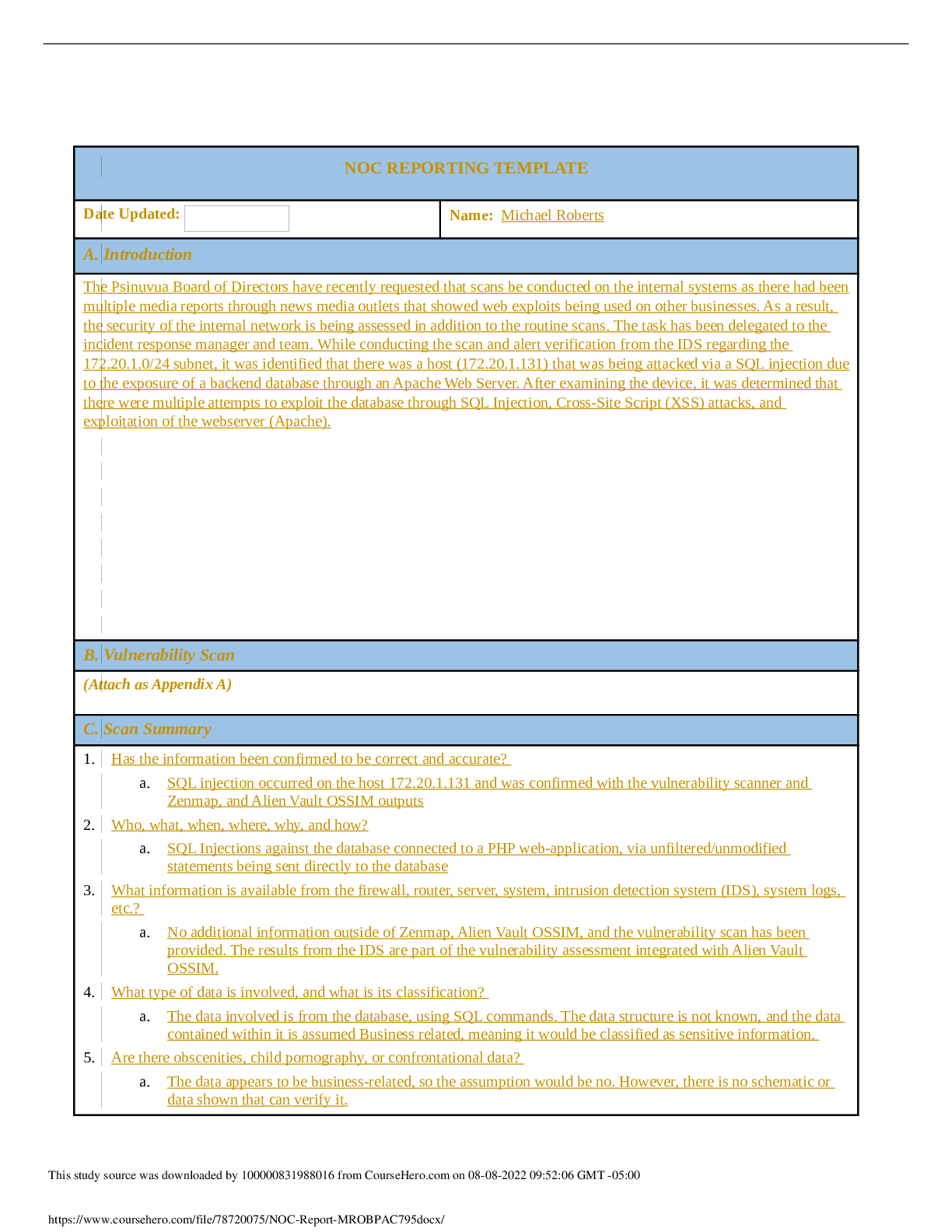
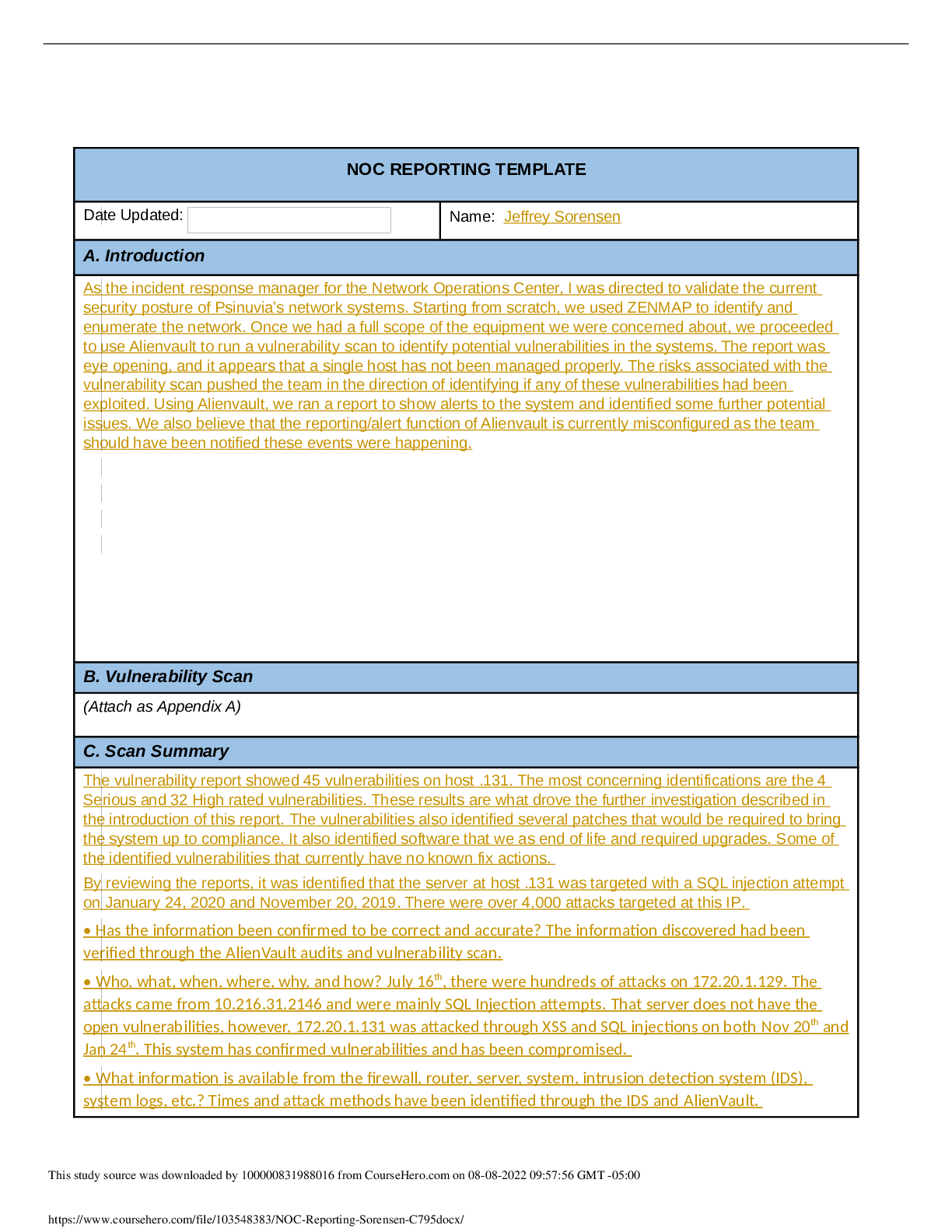
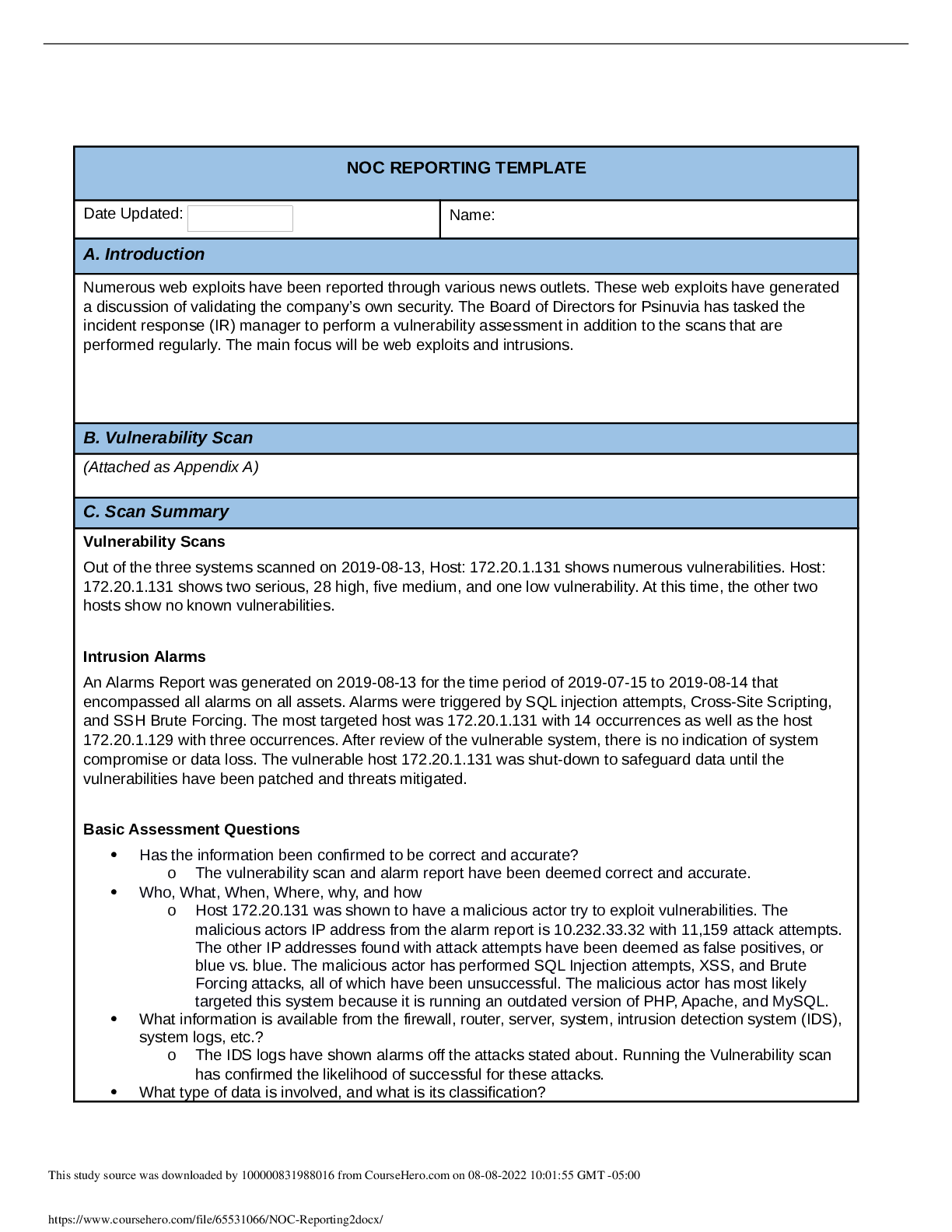
NOC REPORTING TEMPLATE Date Updated: 3/22/2021 Name: Bruce Bracey A. Introduction Vulnerabilities were detected on one of the web servers during a security validation scan requested by the Board o... f Directors for Psinuvia. B. Vulnerability Scan Appendix A.pdf (Attach as Appendix A) C. Scan Summary The scan found multiple vulnerabilities on the 172.20.1.131 host, including 4 serious, 32 high, 8 medium and 1 low level vulnerability. Vulnerabilities include Apache HTTP Server Mail server answering to VRFY and EXPN requests DCE/RPC and MSRPC Services Enumeration FTP Unencrypted Login IMAP Unencrypted Logins POP3 Unencrypted Logins Microsoft SMB Server Vulnerabilities Multiple OpenSSL issues Multiple PHP issues phpinfo output accessible Expired SSL certificate SSL certificate using a weak signature algorithm Untrusted SSL certificate authority Vulnerability in DSA signature generation Http TRACE XSS attach vulnerability The information was confirmed to be correct as it was obtained by a requested security validation scan performed for the Network Operations Center (NOC) for Psinuvia. The scan was performed with Kali Linux tools on 2020-01-24 at 20:07 by the incident response manager for Psinuvia from the Psinuvia NOC at the request of the Board of Directors for Psinuvia. Information was retrieved from Zenmap and AlienVault OSSIM scans and is included in Appendix A of this document. Data involved is the scan results of the network and a list of vulnerabilities. There were no obscenities, child pornography, or confrontational data found in the scan. There is no obvious criminal activity. The scans did not verify if data was encrypted, but it did find that This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 10:08:13 GMT -05:00 https://www.coursehero.com/file/107942490/C795-Task1rtf/ FTP, IMAP and POP3 are using unencrypted logins. The magnitude is one server has multiple vulnerabilities that could be exploited. The vulnerabilities still require remediation. Containment has not been accomplished and will only be possible after patching/updating of the system is complete. The estimated cost is the time required for patching/updating the system. D. Detailed Analysis A scan was performed with Zenmap using the ‘intense scan’ option to obtain a list of hosts on the 172.20.1.0/24 network from a KALI Linux server. bbracey_C795_Task1_part1_000201576.pdf Once complete, a vulnerability scan from AlienVault OSSIM was run against the hosts in the 172.20.1.0/24 network, returning a list of hosts and a count of vulnerabilities. bbracey_C795_Task1_part2_000201576.pdf Finally, a report was generated from the alarms in the scan using AlienVault OSSIM: bbracey_C795_Task1_part3_000201576.pdf The results were recorded in Appendix A of the vulnerability scan section of this document. This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 10:08:13 GMT -05:00 https://www.coursehero.com/file/107942490/C795-Task1rtf/ E. Scan Response The event level for this scan is low as there has been no loss of data, network disruption or other malicious activity. However, the director of Security Ops should be made aware of the results within 72 hours of the scan completion. F. Remediation The 172.20.1.131 host should be taken offline for patching and updates during a scheduled maintenance window as the other hosts in the scan do not support redundant services. 173.20.1.129 is running an Apache server, but it is unclear if the content is the same as 172.20.1.131 as it is running Ubuntu. It does not run FTP or a mail server. 172.20.1.132 does not run HTTP, FTP or a mail server. During patching/updates, FTP and mail This study source was downloaded by 100000831988016 from CourseHero.com on 08-08-2022 10:08:13 GMT -05:00 https://www.coursehero.com/file/107942490/C795-Task1rtf/ will be unavailable so this should be scheduled for after hours or over a weekend. G. Recommendations Administrative Controls: In addition to the regular intrusion scans of systems, a vulnerability scan should also be scheduled at least quarterly. This scan should be reviewed and the actions taken to update/patch systems. Applications on the servers should periodically be reviewed for versioning to verify they are current and none are reaching end-of-life. SSL certificates renewals should be documented and reviewed quarterly to ensure certificates do not [Show More]
Last updated: 1 year ago
Preview 1 out of 5 pages
Instant download
Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Aug 08, 2022
Number of pages
5
Written in
Additional information
This document has been written for:
Uploaded
Aug 08, 2022
Downloads
0
Views
91

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)