Social Sciences > QUESTIONS & ANSWERS > Cyber Awareness Challenge 2022 Already Passed (All)
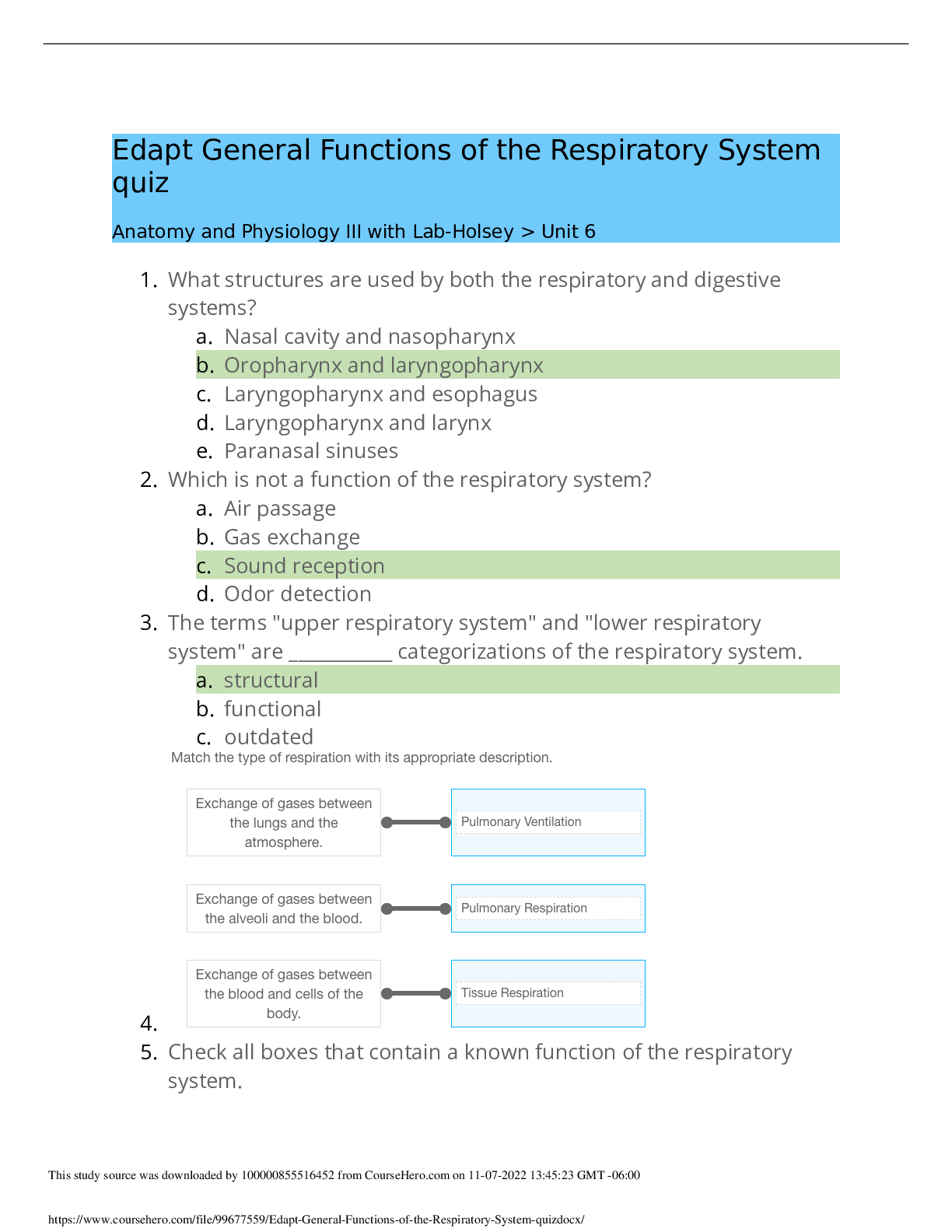
Cyber Awareness Challenge 2022 Already Passed
Document Content and Description Below
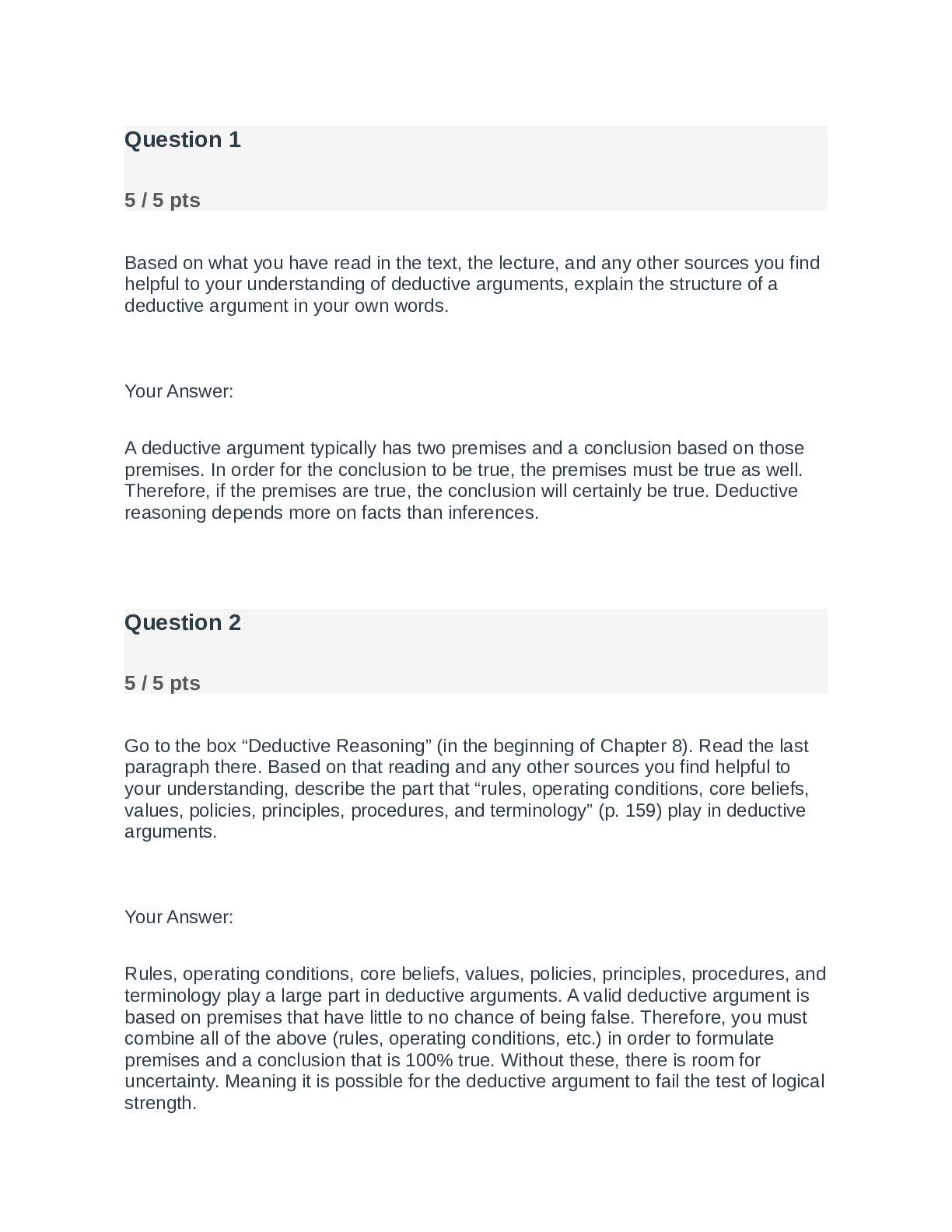
Cyber Awareness Challenge 2022 Already Passed What do you do if spillage occurs? ✔✔Immediately notify your security point of contact. What should you do after you have ended a call from a repor... ter asking you to confirm potentially classified information found on the web? ✔✔Alert your security point of contact. Which of the following is NOT a requirement for telework? ✔✔You must possess security clearance eligibility to telework. Who can be permitted access to classified data? ✔✔Only persons with appropriate clearance, a non-disclosure agreement, and need-to-know can access classified data. A colleague has won 10 high-performance awards, can be playful and charming, is not currently in a relationship, and is occasionally aggressive in trying to access sensitive information. How many potential insiders threat indicators does this employee display? ✔✔1 indicator A colleague has visited several foreign countries recently, has adequate work quality, speaks openly of unhappiness with U.S. foreign policy, and recently had his car repossessed. How many potential insiders threat indicators does this employee display? ✔✔3 or more indicators A colleague complains about anxiety and exhaustion, makes coworkers uncomfortable by asking excessive questions about classified projects, and complains about the credit card bills that his wife runs up. How many potential insiders threat indicators does this employee display? ✔✔3 or more indicators In setting up your personal social networking service account, what email address should you use? ✔✔Your personal email address What information most likely presents a security risk on your personal social networking profile? ✔✔Your place of birth Which of the following is NOT an example of sensitive information? ✔✔Press release data Is it permitted to share an unclassified draft document with a non-DoD professional discussion group? ✔✔As long as the document is cleared for public release, you may release it outside of DoD Which of the following is an example of Protected Health Information (PHI)? ✔✔I've tried all the answers and it still tells me off. Examples are: Patient names, Social Security numbers, Driver's license numbers, insurance details, and birth dates Which of the following represents a good physical security practice? ✔✔Use your own security badge, key code, or Common Access Card (CAC)/Personal Identity Verification (PIC) card. Which of the following is NOT a good way to protect your identity? ✔✔Use a single, complex password for your system and application logons. Which of the following statements is TRUE about the use of DoD Public Key Infrastructure (PKI) tokens? ✔✔Always use DoD PKI tokens within their designated classification level. Which of the following is NOT a typical means for spreading malicious code? ✔✔Patching from a trusted source Which of the following is a practice that helps to protect you from identity theft? ✔✔Ordering a credit report annually Which of the following is a practice that helps to prevent the download of viruses and other malicious code when checking your email? ✔✔Do not access links or hyperlinked media such as buttons and graphics in email messages. You receive an unexpected email from a friend: "I think you'll like this: https://tinyurl.com/2fcbvy." What action should you take? ✔✔Use TinyURL's preview feature to investigate where the link leads. You receive an email from the Internal Revenue Service (IRS) demanding immediate payment of back taxes of which you were not aware. The email provides a website and a toll-free number where you can make payment. What action should you take? ✔✔Contact the IRS When using your government-issued laptop in public environments, with which of the following should you be concerned? ✔✔The potential for unauthorized viewing of work-related information displayed on your screen. Under what circumstances is it acceptable to check personal email on Government-furnished equipment (GFE)? ✔✔If your organization allows it. Which of the following is NOT a best practice to protect data on your mobile computing device? ✔✔Lock your device screen when not in use and require a password to reactivate. When checking in at the airline counter for a business trip, you are asked if you would like to check your laptop bag. This bag contains your government-issued laptop. What should you do? ✔✔I've tried all the answers and it still tells me off, part 2. Decline So That You Maintain Physical Control of Your Government-Issued Laptop. How can you protect your information when using wireless technology? ✔✔Avoid using nonBluetooth-paired or unencrypted wireless computer peripherals. Are you a Boot B*cht? ✔✔Yes [Show More]
Last updated: 1 year ago
Preview 1 out of 4 pages
Instant download
.png)
Instant download
Also available in bundle (1)
.png)
(Solved) Cyber Awareness Challenge Bundled Exams Questions and Answers All Rated A+
(Solved) Cyber Awareness Challenge Bundled Exams Questions and Answers All Rated A+
By Nutmegs 1 year ago
$17
12
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Sep 24, 2022
Number of pages
4
Written in
Additional information
This document has been written for:
Uploaded
Sep 24, 2022
Downloads
0
Views
105

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)

.png)

.png)
.png)
.png)