Information Technology > QUESTIONS & ANSWERS > IT Security: Defense against the digital dark arts. Week4: Securing Your Networks (All)
IT Security: Defense against the digital dark arts. Week4: Securing Your Networks
Document Content and Description Below
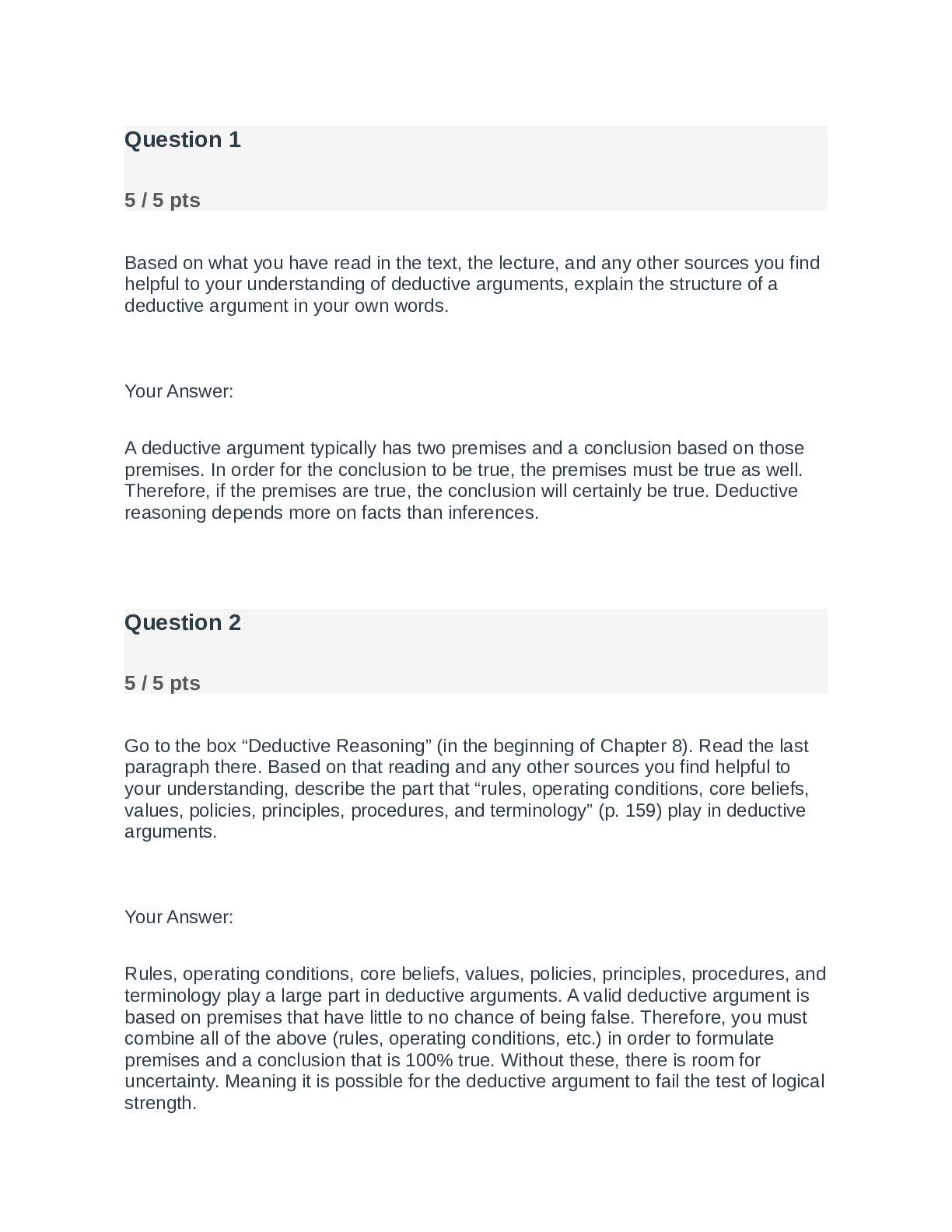
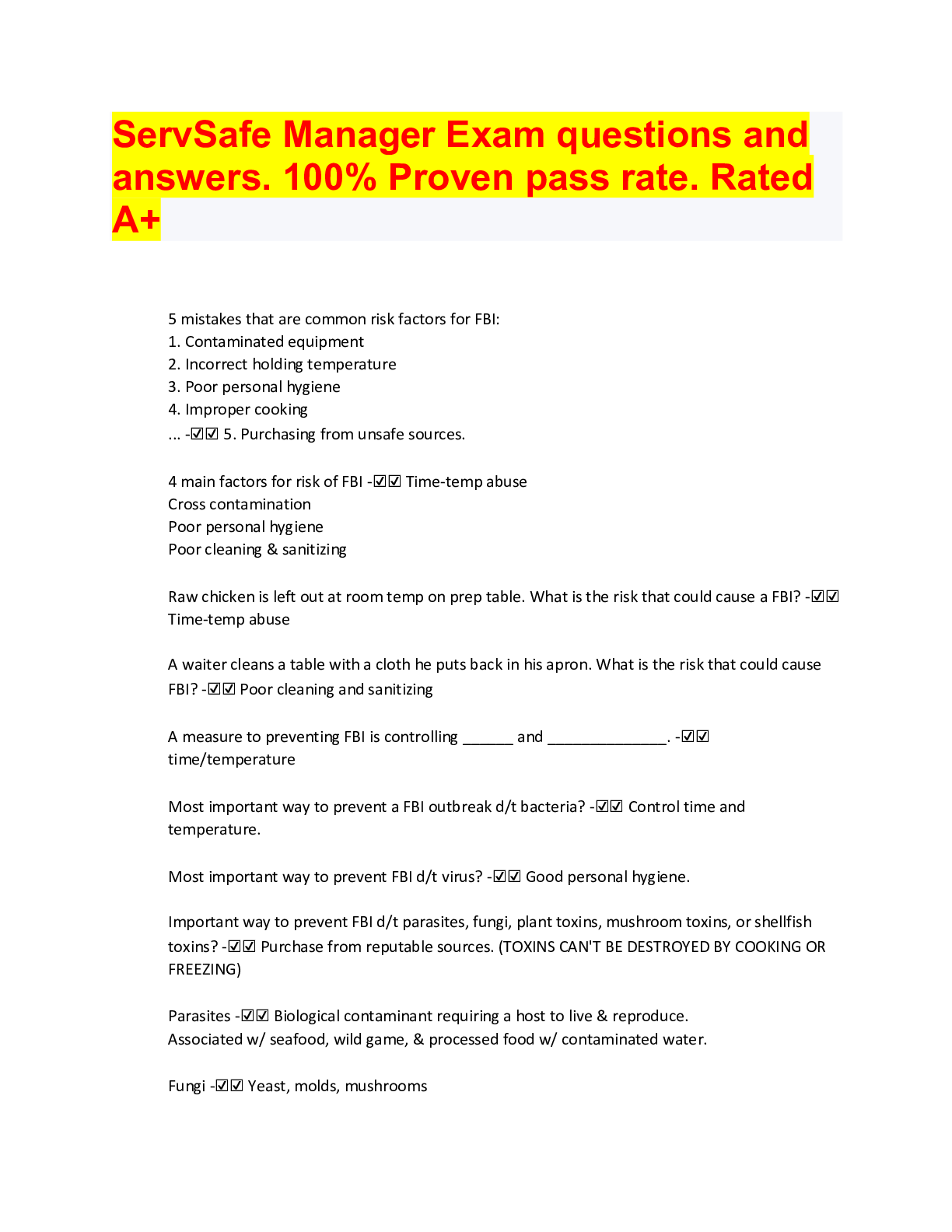
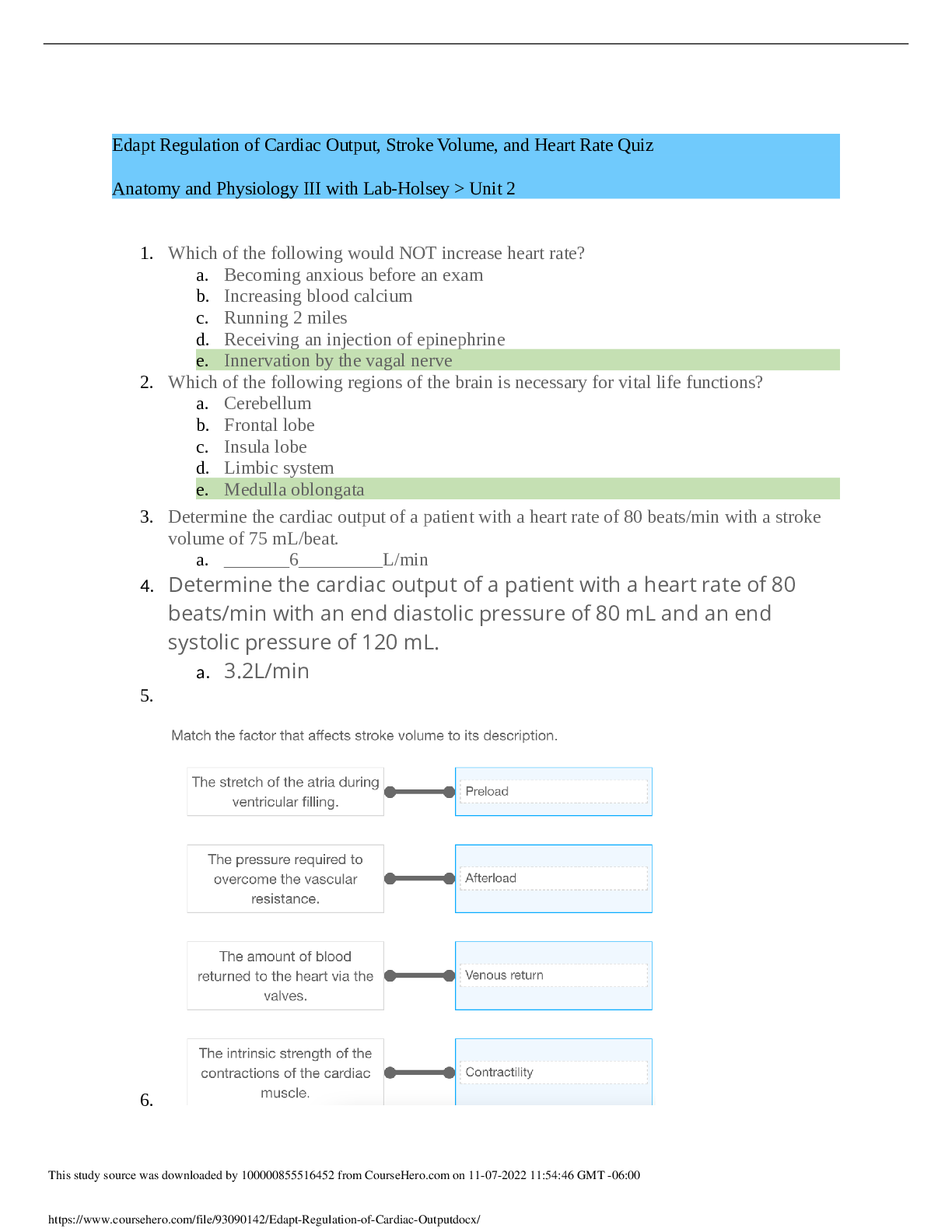
IT Security: Defense against the digital dark arts. Week4: Securing Your Networks Why is normalizing log data important in a centralized logging setup? its difficult to analyze abnormal logs log ... normalizing detects potential attacks the data must be decrypted before sending it to the log server uniformly formatted logs are easier to store and analyze ✔✔its difficult to analyze abnormal logs; Incorrect Not quite. Normalization, in this context, means making the format of logs uniform between systems. What type of attacks does a flood guard protect against? Check all that apply. Malware infections DDos Attacks SYN floods Man-in-the-middle attacks ✔✔DDoS Attacks; A flood guard protects against attacks that overwhelm networking resources, like DoS attacks and SYN floods. You didn't select all the correct answers What does DHCP Snooping protect against? ✔✔Rogue DHCP server attacks; DHCP snooping is designed to guard against rogue DHCP attacks. The switch can be configured to transmit DHCP responses only when they come from the DHCP server's port. What does Dynamic ARP Inspection protect against? ✔✔ARP poisoning attacks; Dynamic ARP inspection protects against ARP poisoning attacks by watching for ARP packets. If an ARP packet doesn't match the table of MAC address and IP address mappings generated by DHCP snooping, the packet will be dropped as invalid or malicious. What does IP Source Guard protect against? ✔✔IP spoofing attacks; IP Source Guard prevents an attacker from spoofing an IP address on the network. It does this by matching assigned IP addresses to switch ports, and dropping unauthorized traffic. What does EAP-TLS use for mutual authentication of both the server and the client? ✔✔digital certificates; The client and server both present digital certificates, which allows both sides to authenticate the other, providing mutual authentication. Why is it recommended to use both network-based and host-based firewalls? Check all that apply. ✔✔for protection for mobile devices, like laptops for protection against compromised hosts on the same network; Using both network- and hostbased firewalls provides protection from external and internal threats. This also protects hosts that move between trusted and untrusted networks, like mobile devices and laptops. What are some of the weaknesses of the WEP scheme? Check all that apply. ✔✔its use of RC4 stream cipher its poor key generation methods its small IV pool size; The RC4 stream cipher had a number of design flaws and weaknesses. WEP also used a small IV value, causing frequent IV reuse. Lastly, the way that the encryption keys were generated was insecure. What symmetric encryption algorithm does WPA2 use? ✔✔AES; WPA2 uses CCMP. This utilizes AES in counter mode, which turns a block cipher into a stream cipher [Show More]
Last updated: 1 year ago
Preview 1 out of 6 pages
Instant download
.png)
Instant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Oct 03, 2022
Number of pages
6
Written in
Additional information
This document has been written for:
Uploaded
Oct 03, 2022
Downloads
0
Views
63

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)

.png)

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)